Security Alert: Daixin Ransomware Targets Healthcare
Data Breach Today
OCTOBER 24, 2022
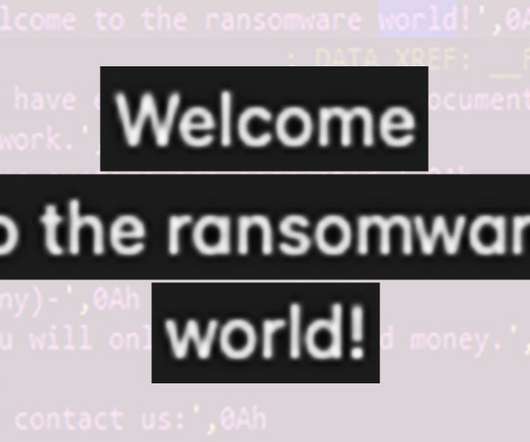
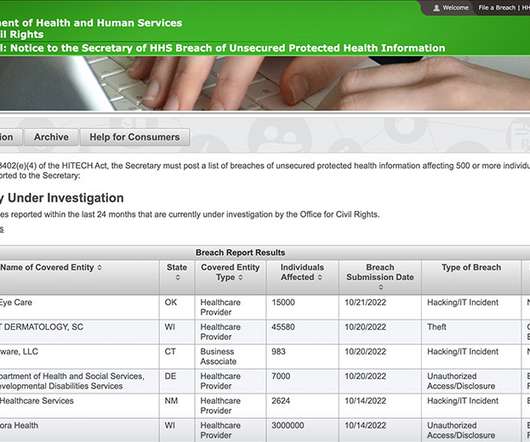
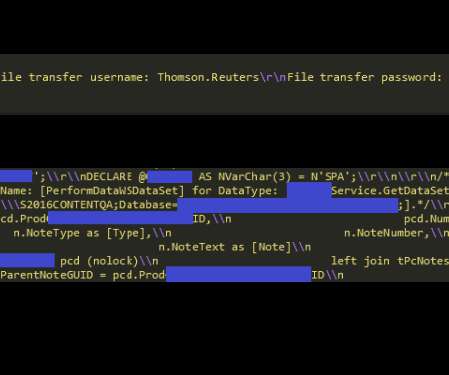
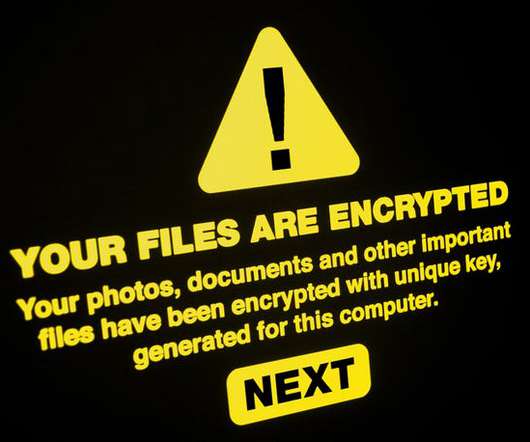
Cybercrime Gang Wields Phishing Emails and Proficiency for VMware Environments Beware ransomware and data extortion shakedowns that trace to a cybercrime gang called Daixin Team, which is especially targeting the healthcare sector, as well as wielding phishing emails and a proficiency with VMware server environments, warns a new U.S. government cybersecurity advisory.





































Let's personalize your content