Ask Fitis, the Bear: Real Crooks Sign Their Malware
Krebs on Security
JUNE 1, 2023
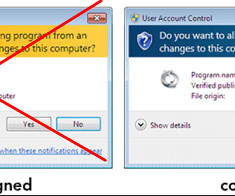
Code-signing certificates are supposed to help authenticate the identity of software publishers, and provide cryptographic assurance that a signed piece of software has not been altered or tampered with. Both of these qualities make stolen or ill-gotten code-signing certificates attractive to cybercriminal groups, who prize their ability to add stealth and longevity to malicious software.









































Let's personalize your content