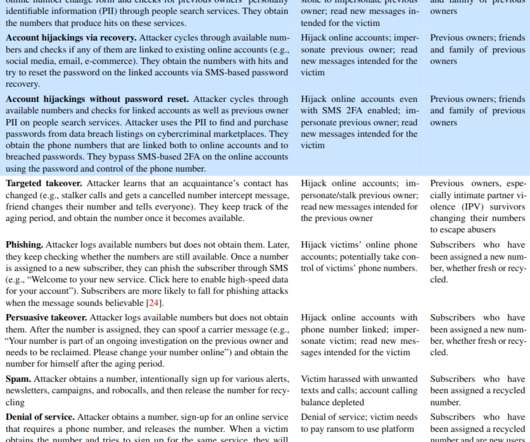
A Closer Look at the DarkSide Ransomware Gang
Krebs on Security
MAY 11, 2021
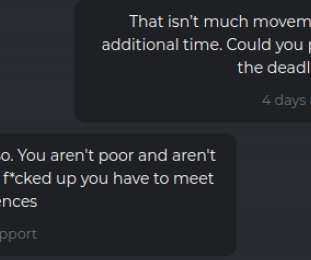
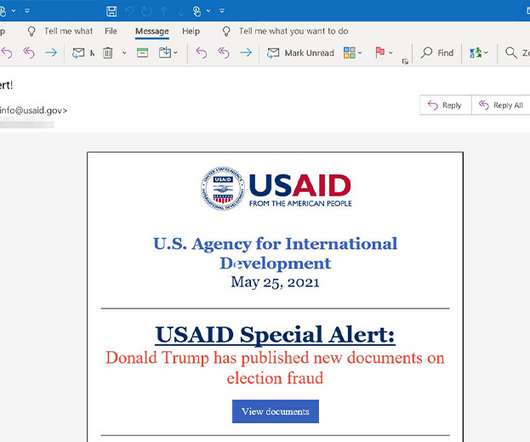
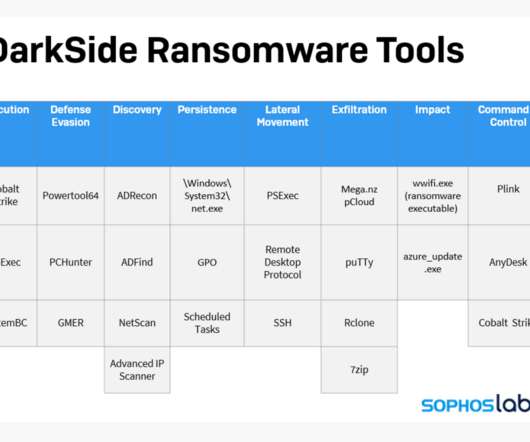
The FBI confirmed this week that a relatively new ransomware group known as DarkSide is responsible for an attack that caused Colonial Pipeline to shut down 5,550 miles of pipe , stranding countless barrels of gasoline, diesel and jet fuel on the Gulf Coast. Here’s a closer look at the DarkSide cybercrime gang, as seen through their negotiations with a recent U.S. victim that earns $15 billion in annual revenue.



































Let's personalize your content