Cybercrime Losses Up 50%, Exceeding $1.8B
Dark Reading
OCTOBER 16, 2020
Fewer companies are being hit by cyber incidents, but those that do get hit are hit harder and more often.

Dark Reading
OCTOBER 16, 2020
Fewer companies are being hit by cyber incidents, but those that do get hit are hit harder and more often.

Data Breach Today
OCTOBER 16, 2020
Labels Will Indicate What Security Standards Products Meet Singapore has launched an IoT cybersecurity labelling program intended to improve the baseline security of internet-connected consumer products. The program is voluntary, but Singapore eventually intends to make it mandatory.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Protector
OCTOBER 16, 2020
I think not. 1. European laws have special rules for the processing of “sensitive data” or “special category data” regardless of the context within which the data will be processed. This has been the case in the UK since the coming into force of the first (1984) Data Protection Act. But, just because it is an established concept, there is no reason not to ask whether the distinction is still appropriate. 2.
Data Breach Today
OCTOBER 16, 2020
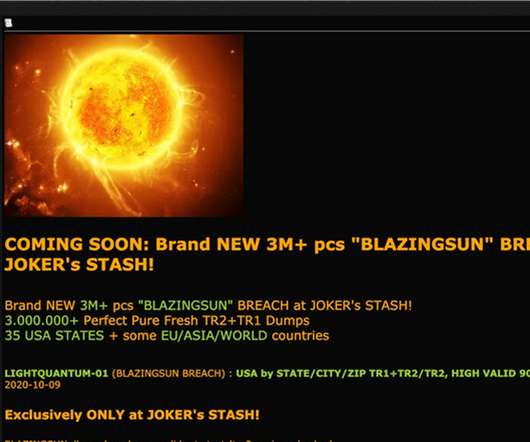
Joker's Stash Darknet Marketplace Offering Payment Cards Used at Franchise Restaurants The Joker's Stash darknet marketplace has posted a fresh collection of 3 million credit cards that are likely related to a breach of the Dickey's Barbecue Pit chain of franchised restaurants, according to Gemini Advisory.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

erwin
OCTOBER 16, 2020
It’s certainly no secret that data has been growing in volume, variety and velocity, and most companies are overwhelmed by managing it, let alone harnessing it to put it to work. We’re now generating 2.5 quintillion bytes of data every day, and 90% of the world’s data volume has been created in the past two years alone. With this absolute data explosion, it’s nearly impossible to filter out the time-sensitive data, the information that has immediate relevance and impact o
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Dark Reading
OCTOBER 16, 2020
Larry Cashdollar, a researcher with more than 300 CVEs to his credit, looks back at his favorite vulnerabilities (and being the only individual CNA on Mitre's list).
Data Breach Today
OCTOBER 16, 2020
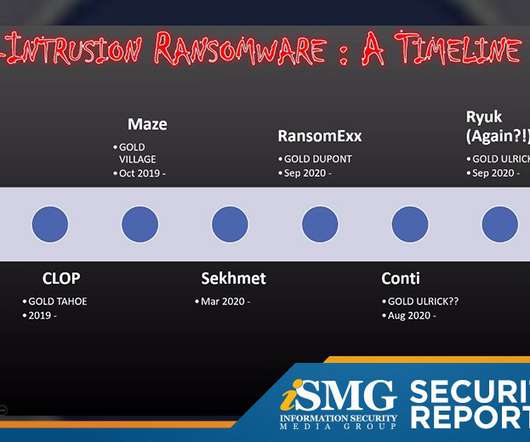
The latest edition of the ISMG Security Report analyzes a new report that labels ransomware as the No. 1 cybercrime threat. Also featured: A former FBI agent offers an update on "disruptionware" attacks; how Tesla's autopilot is tricked by phantom images.

Security Affairs
OCTOBER 16, 2020
The Tripwire VERT security team spotted almost 800,000 SonicWall VPN appliances exposed online that are vulnerable to the CVE-2020-5135 RCE flaw. Security experts from the Tripwire VERT security team have discovered 795,357 SonicWall VPN appliances that were exposed online that are vulnerable to the CVE-2020-5135 RCE flaw. “A buffer overflow vulnerability in SonicOS allows a remote attacker to cause Denial of Service (DoS) and potentially execute arbitrary code by sending a malicious reque

Data Breach Today
OCTOBER 16, 2020
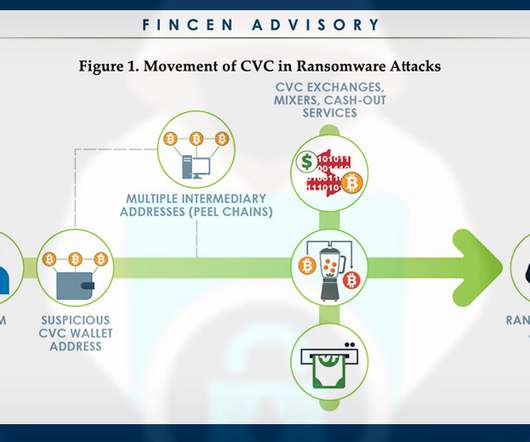
Physical Attacks Increase in US; ATM Malware and Logical Attacks Rise in Europe Criminals have been seeking innovative new ways to steal cash from ATMs. In the U.S., there has been a surge in physical attacks, while Europe has seen a sharp increase in "black box" attacks designed to make ATMs dispense cash on demand.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Hunton Privacy
OCTOBER 16, 2020
On October 15, 2020, Brazil’s President Bolsonaro officially nominated the five Directors of the new Brazilian data protection authority ( Agência Nacional de Proteção de Dados , “ANPD”), as published in the Brazilia Official Journal. The Decree establishing the ANPD, on which we reported earlier , is now fully in effect. All five nominations, however, must still be approved by the Brazilian Senate, which means there are further steps before the ANPD is fully established and operational.
Data Breach Today
OCTOBER 16, 2020
Here's Why Stopping the Extortion Epidemic Isn't Easy As ransomware continues to slam organizations, a lively debate has ensued about whether ransom payments should be banned in all cases. Attempting to ban ransom payments, however, likely would only make the problem worse.

Adam Levin
OCTOBER 16, 2020
Barnes & Noble has confirmed a data breach following a cyberattack that took many of their services offline. . The bookseller sent an email to customers notifying them that their personal information had been exposed, but that their financial information had not been compromised. . “While we do not know if any personal information was exposed as a result of the attack, we do retain in the impacted systems your billing and shipping addresses, your email address and your telephone number if yo

Data Breach Today
OCTOBER 16, 2020
Many healthcare organizations are failing to address shortcomings in security risk management for their supply chains, says former healthcare CIO David Finn, describing findings of a recent study assessing the state of cybersecurity in the sector.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
Security Affairs
OCTOBER 16, 2020
Dickey’s Barbecue Pit, the largest barbecue restaurant chain in the US, suffered a POS breach, card details for 3 Million customers were posted online. Dickey’s Barbecue Pit is a family-owned American barbecue restaurant chain, the company suffered a POS breach and card details of more than three million customers have been posted on the carding portal Joker’s Stash.

Data Breach Today
OCTOBER 16, 2020
Fined $26 Million in Connection With 2018 Breach Britain's Information Commissioner's Office announced this week a dramatic reduction in its fine against British Airways for violating the EU's General Data Protection Regulation. The company will pay a $26 million fine instead of $238 million in a case tied to a 2018 breach.

Security Affairs
OCTOBER 16, 2020
Britain’s information commissioner has fined British Airways 20 million pounds for the 2018 hack that exposed data of 400,000 customers. In September 2018, British Airways suffered a data breach that exposed the personal information of 400,000 customers. The hackers potentially accessed the personal data of approximately 429,612 customers and staff.

Dark Reading
OCTOBER 16, 2020
Larry Cashdollar, a researcher with more than 300 CVEs to his credit, looks back at his favorite vulnerabilities (and being the only individual CNA on Mitre's list).

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Security Affairs
OCTOBER 16, 2020
Adobe released a series of out-of-band security fixes to address multiple Magento vulnerabilities that lead to code execution, customer list tampering. Adobe has released a series of out-of-band security fixes to address multiple Magento vulnerabilities that lead to code execution, customer list tampering. Eight of the vulnerabilities are considered either critical or important, only one is considered a moderate-severity flaw.

Threatpost
OCTOBER 16, 2020
The two important-severity flaws in Microsoft Windows Codecs Library and Visual Studio Code could enable remote code execution.
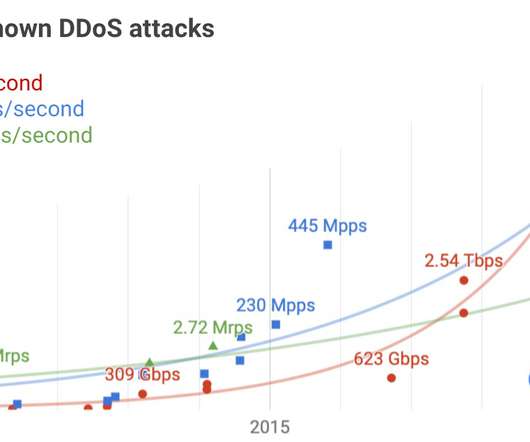
Security Affairs
OCTOBER 16, 2020
The Google Cloud team revealed that in September 2017 it has mitigated DDoS attack that reached 2.54 Tbps, the largest DDoS attack of ever. The Google Cloud team revealed that back in September 2017 it has mitigated a powerful DDoS attack that clocked at 2.54 Tbps. This attack is the largest distributed denial of service attack recorded to date. “Our infrastructure absorbed a 2.5 Tbps DDoS in September 2017, the culmination of a six-month campaign that utilized multiple methods of attac

Threatpost
OCTOBER 16, 2020
After cybercriminals smoked out 3 million compromised payment cards on the Joker’s Stash marketplace, researchers linked the data to a breach at the popular barbecue franchise.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

WIRED Threat Level
OCTOBER 16, 2020
Nice looking website you've got there. It'd be a shame if someone DDoS'd it.

Threatpost
OCTOBER 16, 2020
Fortinet researchers are seeing a pivot in the spear-phishing and phishing lures used by cybercriminals, to entice potential job candidates as businesses open up.

Dark Reading
OCTOBER 16, 2020
Security pros and academic researchers discuss the best ways to use MITRE's framework to inform cybersecurity efforts, analyze threats, and teach future workers.

WIRED Threat Level
OCTOBER 16, 2020
The company’s flip-flopping on the policy after banning a shady New York Post story highlights the challenges facing social media in 2020.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Dark Reading
OCTOBER 16, 2020
The US counterintelligence lead joins a former Europol cyber chief to discuss modern election threats and the benefits of public-private collaboration.

Threatpost
OCTOBER 16, 2020
The move is a distinct change in direction for the app, which has been criticized and even banned for its security practices.

Security Affairs
OCTOBER 16, 2020
Juniper Networks has addressed tens of vulnerabilities, including serious flaws that can be exploited to take over vulnerable systems. Juniper Networks has addressed tens of vulnerabilities, including serious issues that can be exploited to take control of vulnerable systems. The vendor has published 40 security advisories related to security vulnerabilities in the Junos OS operating system that runs on Juniper’s firewalls and other third-party components.
Let's personalize your content