Babuk Ransomware Gang Posts More DC Metro Police Data
Data Breach Today
MAY 12, 2021
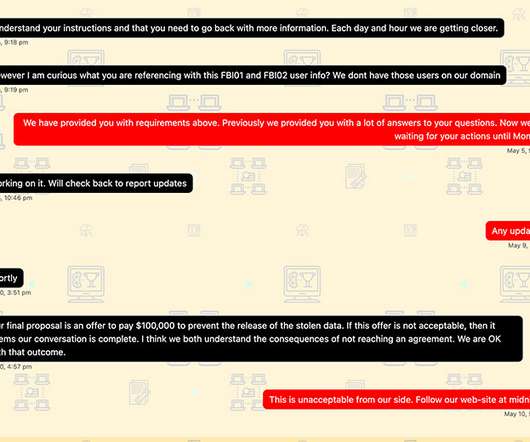
Babuk Has Threatened to Release More MPD Info The Babuk ransomware gang has reignited its feud with the Washington, D.C. Metropolitan Police Department by posting what it says is an additional 22GB of stolen data and what it claims is a transcript of the failed ransom negotiations.





































Let's personalize your content