Are You Prepared to Defend Against a USB Attack?
Dark Reading
JANUARY 24, 2022
Recent "BadUSB" attacks serve as a reminder of the big damage that small devices can cause.

Dark Reading
JANUARY 24, 2022
Recent "BadUSB" attacks serve as a reminder of the big damage that small devices can cause.

The Last Watchdog
JANUARY 24, 2022
Artificial intelligence (AI) is woven into the fabric of today’s business world. However, business model integration of AI is in its infancy and smaller companies often lack the resources to leverage AI. Related: Deploying human security sensors. Even so, AI is useful across a wide spectrum of industries. There already are many human work models augmented by AI.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Thales Cloud Protection & Licensing
JANUARY 24, 2022
Data Privacy and Security: It Takes Two to Tango. madhav. Tue, 01/25/2022 - 05:15. The National Cybersecurity Alliance (NCA) announced earlier this year that they have expanded the Data Privacy Day campaign into Data Privacy Week , a full week-long initiative. Data Privacy Day began in the United States and Canada in January 2008 as an extension of Data Protection Day in Europe.

Hunton Privacy
JANUARY 24, 2022
On January 7, 2022, U.S. Representatives Kathy Castor (D-Fla.) and Jan Schakowsky (D-Ill.), members of the House Committee on Energy and Commerce, wrote to all of the Children’s Online Privacy Protection Act (“COPPA”) Safe Harbor programs to request information about each program to ensure “participants in the program are fulfilling their legal obligations to provide ‘substantially the same or greater protections for children’ as those detailed in the COPPA Rule” and “to solicit feedback” regard

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.
Security Affairs
JANUARY 24, 2022
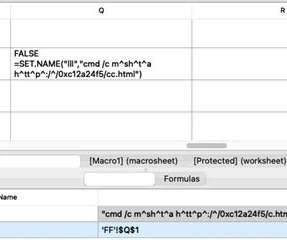
Experts warn Emotet malware campaign using “unconventional” IP address formats in an attempt to evade detection. Threat actors behind a recent Emotet malware campaign have been observed using using “unconventional” IP address formats to evade detection. Trend Micro researchers reported that threat actors are using hexadecimal and octal representations of the IP address. “We observed Emotet spam campaigns using hexadecimal and octal representations of IP addresses, l
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

IT Governance
JANUARY 24, 2022
Data privacy is a concept that governs our everyday lives. We’re asked to hand over our personal data for seemingly everything that we do – from browsing the web to high-street shopping. Although many of us are broadly aware of the risks involved when sharing our personal data, it often doesn’t get the attention it deserves. It’s why, for the past fifteen years, 28 January has marked Data Privacy Day – an international event raises awareness about online privacy and educates people on the ways t

Security Affairs
JANUARY 24, 2022
Russian authorities arrested four alleged members of the international cyber theft ring tracked as ‘Infraud Organization.’ In February 2008, the US authorities dismantled the global cybercrime organization tracked as Infraud Organization, which was involved in stealing and selling credit card and personal identity data. The Justice Department announced indictments for 36 people charged with being part of a crime ring.

Gimmal
JANUARY 24, 2022
The need to secure a document for legal holds or to meet industry-specific records compliance is not a new concept for records managers. Historically, records managers had relied on the “immutable records” approach for ensuring compliant records management. However, with the growing popularity of the “preservation copy” approach of securing records while allowing end-users to continue working on the documents, many are considering the differences between the two strategies to determine which is

Security Affairs
JANUARY 24, 2022
A new version of the BRATA malware implements a functionality to perform a factory reset of the device to wipe all data. The new version of the BRATA Android malware supports new features, including GPS tracking and a functionality to perform a factory reset on the device. Security experts at Kaspersky discovered the Android RAT BRATA (the name comes from ‘Brazilian RAT Android’) in 2019, when it was used to spy on Brazilian users.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Dark Reading
JANUARY 24, 2022
Security professionals need to understand the actors behind ransomware threats, how they operate and how they continuously find new victims to target

Security Affairs
JANUARY 24, 2022
Threat actors planted a backdoor into multiple WordPress themes and plugins after compromising the website of their developer. In a classic supply chain attack, threat actors planted a backdoor in dozens of WordPress plugins and themes hosted on a developer’s website. The attack took place in the first half of September 2021, the attackers compromised 40 themes and 53 plugins belonging to AccessPress Themes.

Dark Reading
JANUARY 24, 2022
The authors of the infamous malware family have added measures for better protecting malicious code injections against inspection and research.

Security Affairs
JANUARY 24, 2022
The maintainers of the Rust programming language fixed a high-severity flaw that could allow attackers to delete files and directories from a vulnerable system. The maintainers of the Rust programming language have released a security update for a high-severity vulnerability, tracked as CVE-2022-21658. An attacker can trigger the vulnerability to delete files and directories from a vulnerable system. “The Rust Security Response WG was notified that the std::fs::remove_dir_all standard lib

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Threatpost
JANUARY 24, 2022
QR codes have become a go-to staple for contactless transactions of all sorts during the pandemic, and the FBI is warning cybercriminals are capitalizing on their lax security to steal data and money, and drop malware.

Dark Reading
JANUARY 24, 2022
As enterprise data security concerns grow, security experts urge businesses to back up their GitLab, GitHub, and BitBucket repositories.

Hunton Privacy
JANUARY 24, 2022
The Austrian data protection authority (the “Austrian DPA”) recently published a decision in a case brought against an Austrian website provider and Google by the non-governmental organization co-founded by privacy activist Max Schrems, None of Your Business (“NOYB”). The Austrian DPA ruled that the use of Google Analytics cookies by the website operator violates both Chapter V of the EU General Data Protection Regulation (“GDPR”), which establishes rules on international data transfers, and the

Dark Reading
JANUARY 24, 2022
New certification validates students' and career changers' foundational skills and helps kickstart their cybersecurity careers.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Threatpost
JANUARY 24, 2022
The two flaws in Control Web Panel – a popular web hosting management software used by 200K+ servers – allow code execution as root on Linux servers.

Dark Reading
JANUARY 24, 2022
As hostilities mount between Russia and Ukraine, new and more dangerous cyberattacks are likely to develop. Pinpointing sources and motives will remain elusive, but enterprises should prepare for an escalation in cyberspace.

Threatpost
JANUARY 24, 2022
The bug can allow attackers to remotely execute code on gamers’ computers. The devs temporarily deactivated PvP servers across multiple affected versions.

OpenText Information Management
JANUARY 24, 2022
2023 will be the year the cookie crumbles. Google announced plans to delay the phase-out of third-party cookies in Chrome, giving marketers just a bit more time to prepare. But does that mean brands are ready? Nearly half (49%) of all US digital media professionals polled by Integral Ad Science in October 2020 cited third-party … The post 6 things for marketers to keep in mind as the third-party cookie crumbles appeared first on OpenText Blogs.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

IG Guru
JANUARY 24, 2022
Check out the article here. The post What is Intelligent Document Processing? via The ECM Consultant appeared first on IG GURU.

Threatpost
JANUARY 24, 2022
State-sponsored cyberattackers are using Google Drive, Dropbox and other legitimate services to drop spyware on Middle-Eastern targets and exfiltrate data.

Dark Reading
JANUARY 24, 2022
Cyberattacks imperil business continuity, but there is a much more common security threat — unintentional human error.

National Archives Records Express
JANUARY 24, 2022
Our office has posted a vacancy announcement for four positions in our appraisal program. The positions will be open until Monday, January 31, 2022. Archives Specialist. Agency: National Archives and Records Administration. Salary: $89,834.00 to $138,868.00 /PA. Series and Grade: GS-1421-12/13. Open Period: Friday January 21, 2022 to Monday, January 31, 2022.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Dark Reading
JANUARY 24, 2022
Ransomware has maintained its dominance the past few years; however, increased law enforcement attention may result in changes to how it looks in the future.
HID Global
JANUARY 24, 2022
Essential Reasons to Upgrade Your Access Control Technology — Reason 1: Security and Data Privacy. jbarton. Mon, 01/24/2022 - 09:57.

Dark Reading
JANUARY 24, 2022
Latest bulletin out of DHS advises state and local governments, critical infrastructure operators to be on alert.
Let's personalize your content