Threat actors can bypass malware detection due to Microsoft Defender weakness
Security Affairs
JANUARY 14, 2022
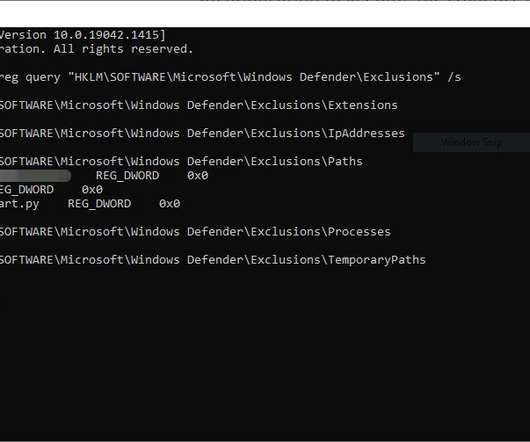
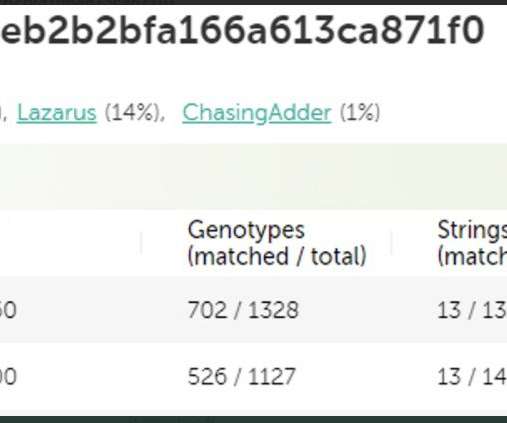
A weakness in the Microsoft Defender antivirus can allow attackers to retrieve information to use to avoid detection. Threat actors can leverage a weakness in Microsoft Defender antivirus to determine in which folders plant malware to avoid the AV scanning. Microsoft Defender allows users to exclude locations on their machines that should be excluded from scanning by the security solution.






































Let's personalize your content