Android Fingerprint Biometrics Fall to 'BrutePrint' Attack
Data Breach Today
MAY 22, 2023
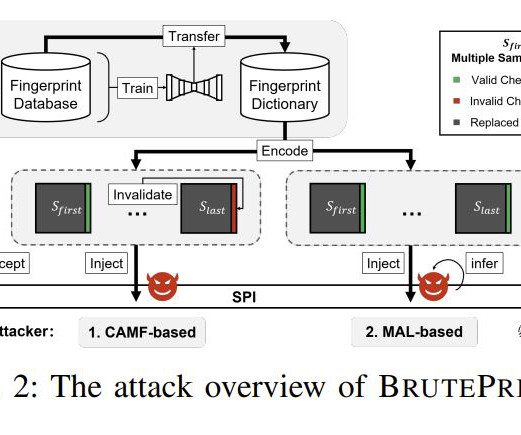
Dictionary Attack Plus Neural Network Fools Security Checks, Researchers Find Security researchers have demonstrated a practical attack that can be used to defeat biometric fingerprint checks and log into a target's Android - but not Apple - smartphone. Dubbed "BrutePrint," the brute force attack is inexpensive and practical to deploy at a large scale.







































Let's personalize your content