COVID-19 Phishing Schemes Escalate; FBI Issues Warning
Data Breach Today
MARCH 23, 2020
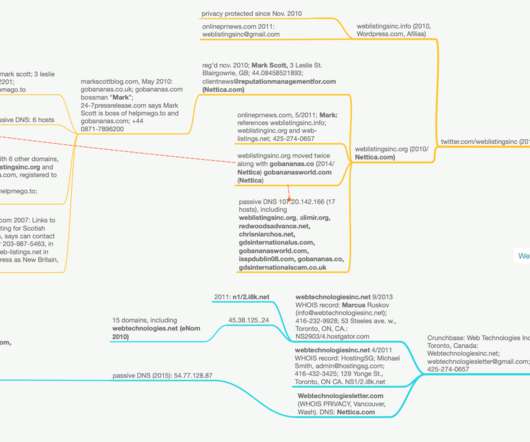
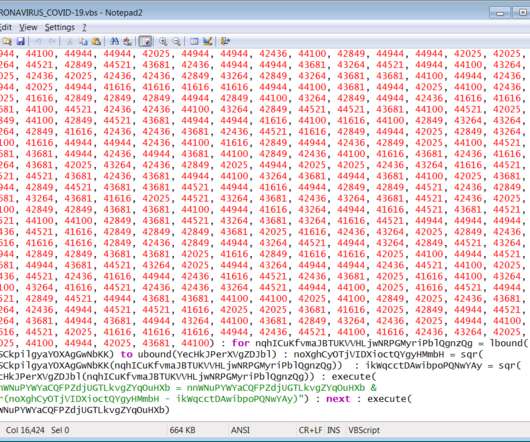
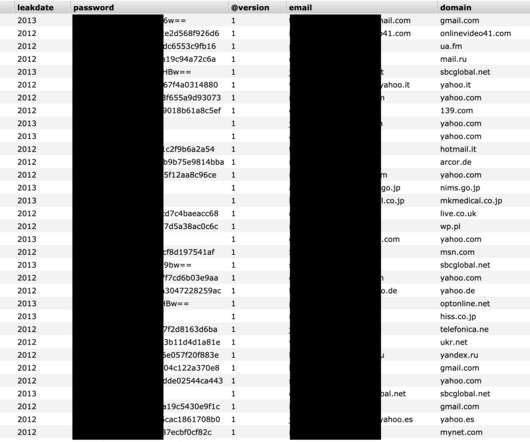
Latest Schemes Target At-Home Employees; Some Spoof Health Agencies As the global COVID-19 pandemic worsens, security firms and law enforcement, including the FBI, are warning of increasing phishing and other the cybercriminal scams targeting a largely at-home workforce.







































Let's personalize your content