Feds Charge NY Man as BreachForums Boss “Pompompurin”
Krebs on Security
MARCH 17, 2023
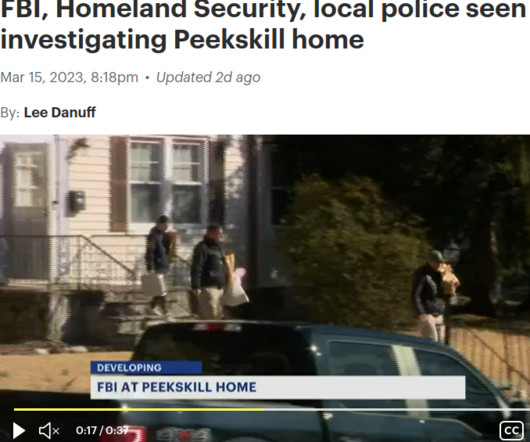
The U.S. Federal Bureau of Investigation (FBI) this week arrested a New York man on suspicion of running BreachForums , a popular English-language cybercrime forum where some of the world biggest hacked databases routinely show up for sale. The forum’s administrator “ Pompompurin ” has been a thorn in the side of the FBI for years, and BreachForums is widely considered a reincarnation of RaidForums , a remarkably similar crime forum that the FBI infiltrated and dismantled in 20






































Let's personalize your content