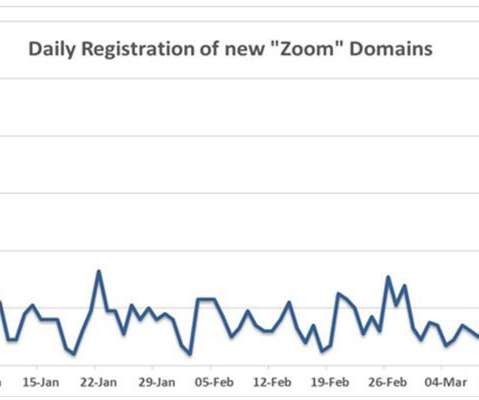
Zoom Stops Transferring Data by Default to Facebook
Data Breach Today
MARCH 30, 2020
Privacy Gaffe Blamed on Facebook's iOS Software Development Kit Zoom has apologized for sharing large sets of user data by default with Facebook, blaming the social network's software development kit, which it has removed from its iOS app. With COVID-19 driving unprecedented levels of remote working, video conferencing software is under the privacy and security microscope.







































Let's personalize your content