When Your Used Car is a Little Too ‘Mobile’
Krebs on Security
FEBRUARY 5, 2020
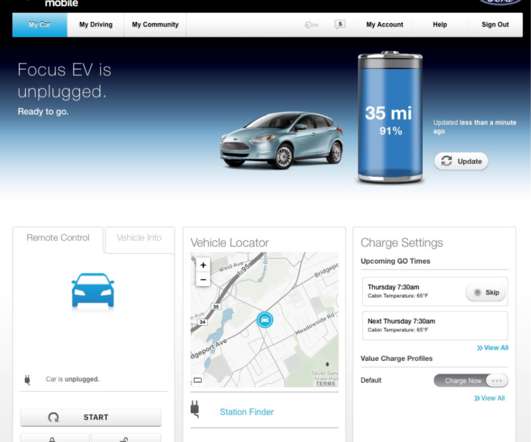
Many modern vehicles let owners use the Internet or a mobile device to control the car’s locks, track location and performance data, and start the engine. But who exactly owns that control is not always clear when these smart cars are sold or leased anew. Here’s the story of one former electric vehicle owner who discovered he could still gain remote, online access to his old automobile years after his lease ended.






































Let's personalize your content