Kaseya Attack: REvil Offers $70 Million 'Super Decryptor'
Data Breach Today
JULY 5, 2021
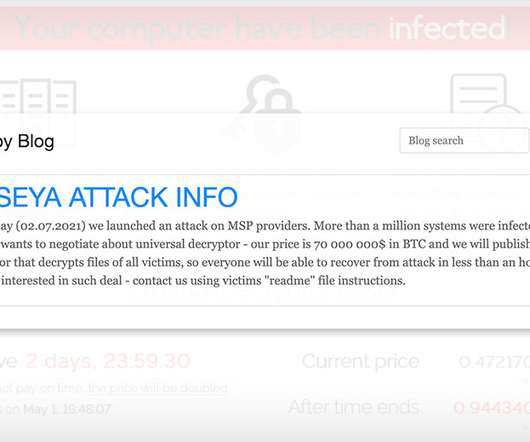
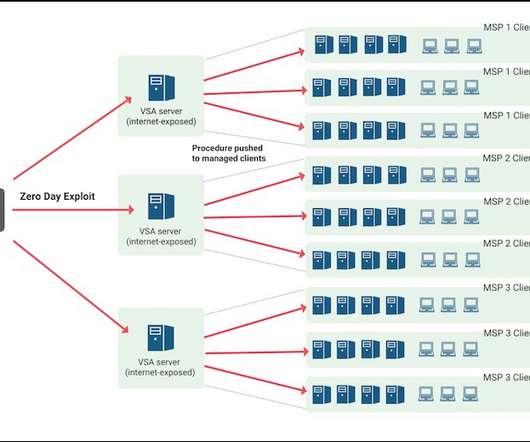
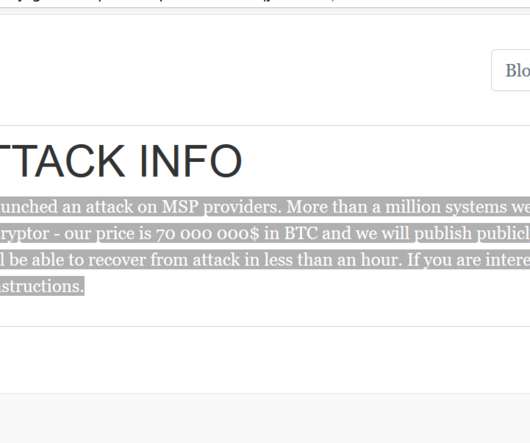
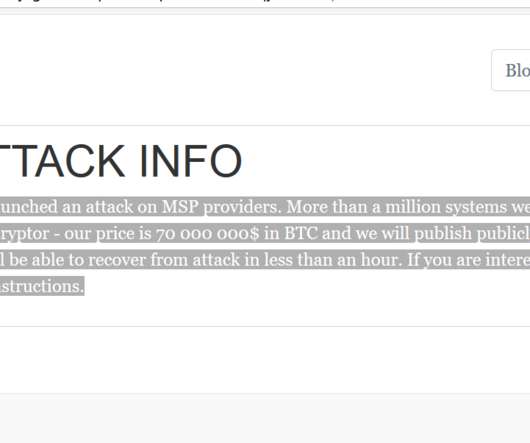
Yet Another Ransomware Attack Targets Managed Service Providers to Maximize Profits The REvil ransomware operation behind the massive attack centering on Kaseya, which develops software used by managed service providers, has offered to decrypt all victims - MSPs as well as their customers - for $70 million in bitcoins. Experts note this isn't the first time REvil has hit MSPs, or even Kaseya.

























Let's personalize your content