Security Blueprints of Many Companies Leaked in Hack of Swedish Firm Gunnebo
Krebs on Security
OCTOBER 28, 2020
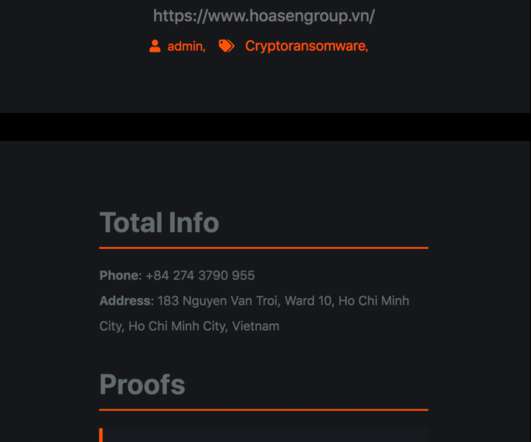
In March 2020, KrebsOnSecurity alerted Swedish security giant Gunnebo Group that hackers had broken into its network and sold the access to a criminal group which specializes in deploying ransomware. Acting on a tip from Milwaukee, Wis.-based What’s more, Syrén seemed to downplay the severity of the exposure.





























Let's personalize your content