Ukraine’s GUR hacked the Russian Ministry of Defense
Security Affairs
MARCH 4, 2024
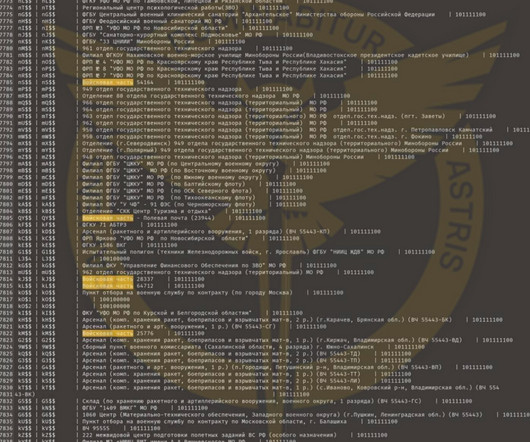
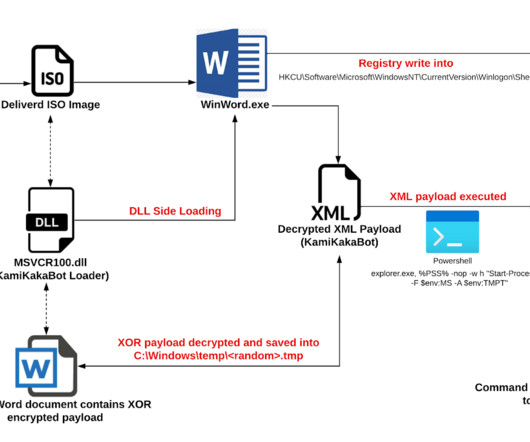
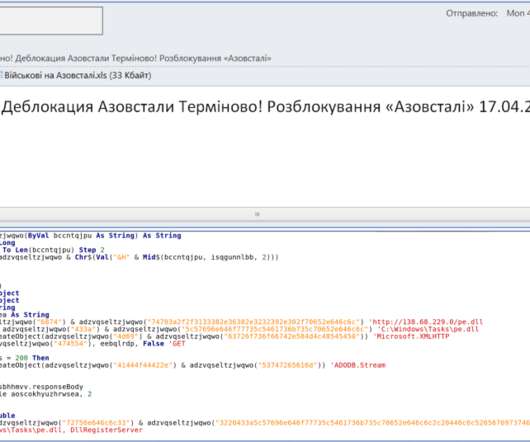
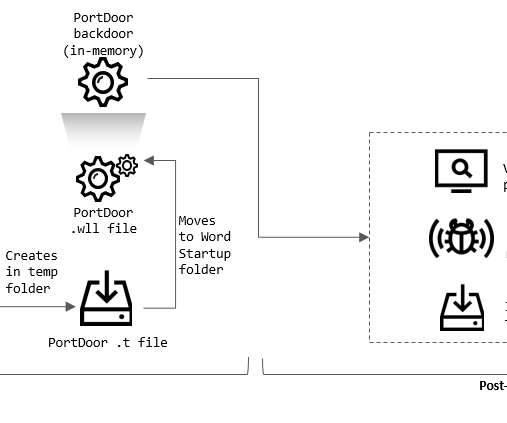
The Main Intelligence Directorate (GUR) of Ukraine’s Ministry of Defense announced it had breached the Russian Ministry of Defense servers as part of a special operation, and exfiltrated confidential documents. software used by the Russian Ministry of Defense to encrypt and protect its data.




































Let's personalize your content