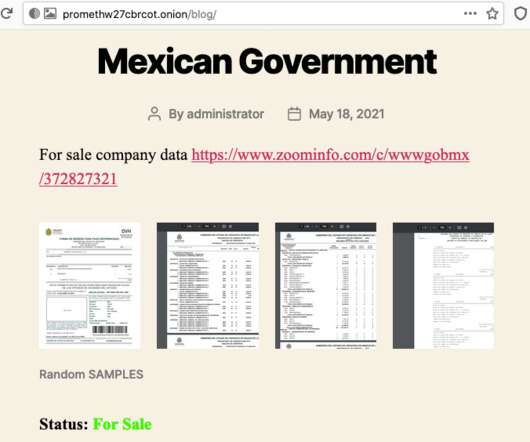
Prometheus and Grief – two new emerging ransomware gangs targeting enterprises. Mexican Government data is published for sale.
Security Affairs
JUNE 1, 2021
According to Resecurity, a cybersecurity company out of Los Angeles, the leaked data has been presumably stolen from multiple e-mail accounts in the result of ATO/BEC and compromise of network resources belonging to several Mexican government agencies. Source: [link]. prometheushelp@airmail.cc Prometheus.help@protonmail.ch






















Let's personalize your content