The DDR Advantage: Real-Time Data Defense
Security Affairs
MARCH 27, 2024
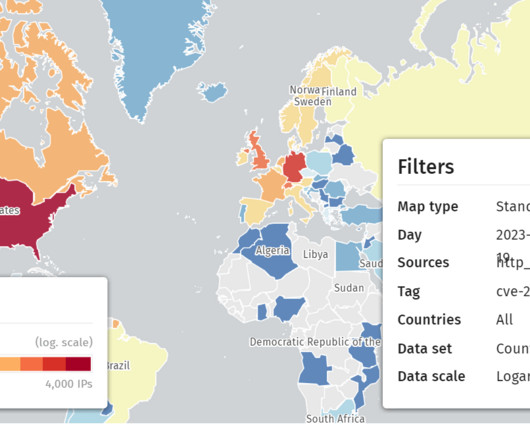
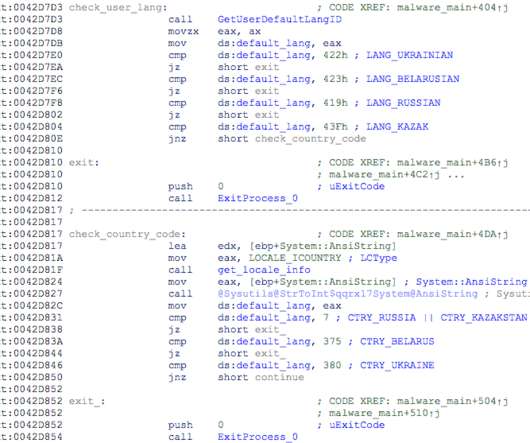
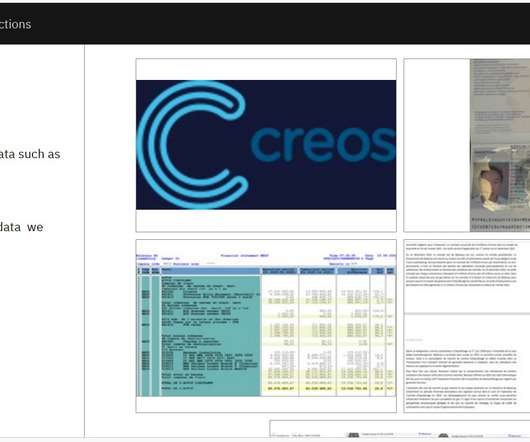
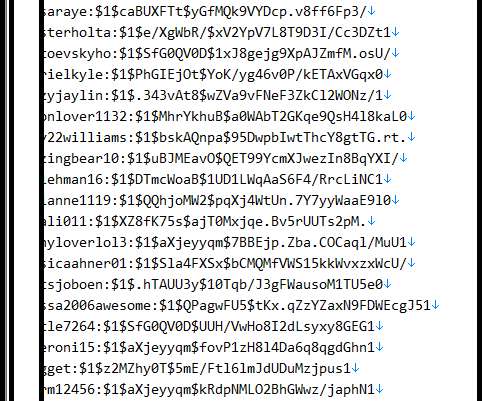
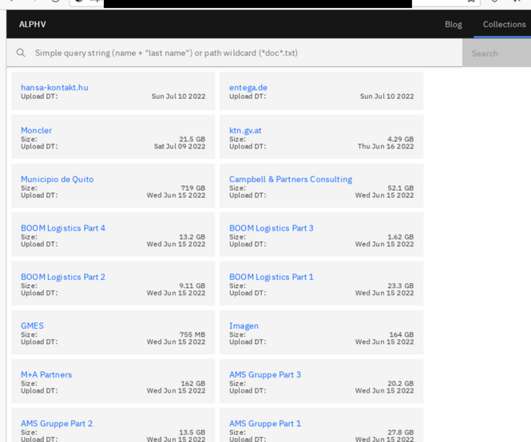
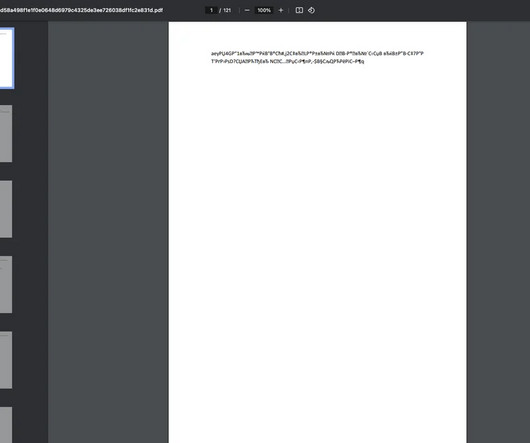
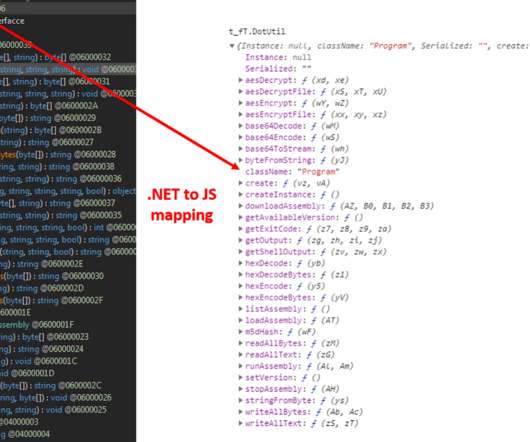
This is the advantage of Data Detection and Response (DDR) for organizations aiming to build a real-time data defense. The advantage of Data Detection and Response (DDR) is that you no longer have to wait until the milk is spilled. With DDR, your organization can have real-time data defense. Here’s how it works.


























Let's personalize your content