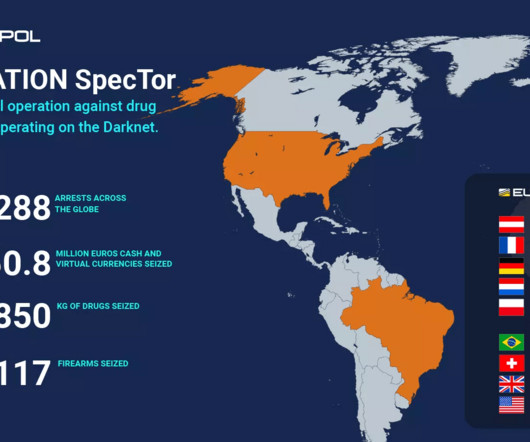
SpecTor operation: 288 individuals arrested in the seizure of marketplace Monopoly Market
Security Affairs
MAY 2, 2023
According to the press release published by the Europol, the seized drugs include over 258 kg of amphetamines, 43 kg of cocaine, 43 kg of MDMA, and over 10 kg of LSD and ecstasy pills. These target packages, created by cross-matching and analysing the collected data and evidence, served as the basis for hundreds of national investigations.”
















Let's personalize your content