China-linked APT Volt Typhoon targets critical infrastructure organizations
Security Affairs
MAY 25, 2023
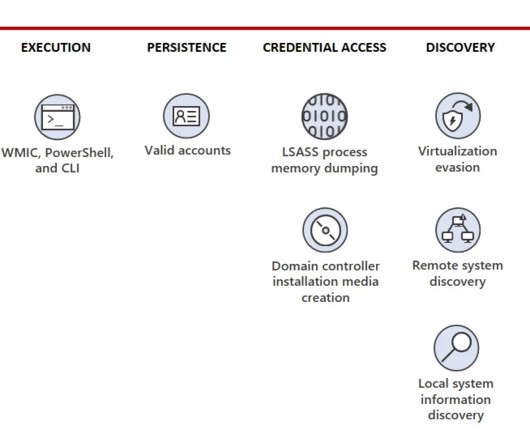
According to Microsoft, the campaign aims at building capabilities that could disrupt critical communications infrastructure between the United States and Asia region in the case of future crises. The group also relies on customized versions of open-source tools for C2 communications and stay under the radar.




















Let's personalize your content