FBI Shares Email Addresses to Speed Emotet Cleanup
Data Breach Today
APRIL 27, 2021
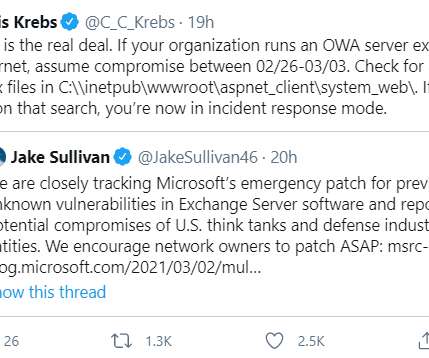
The entry of those addresses into the site increases the chance that those infected with Emotet can take remediation actions, such as changing passwords. Bureau Shares Emails of Those Affected With Have I Been Pwned Breach Notification Service The FBI has shared 4.3
























Let's personalize your content