At Least 30,000 U.S. Organizations Newly Hacked Via Holes in Microsoft’s Email Software
Krebs on Security
MARCH 5, 2021
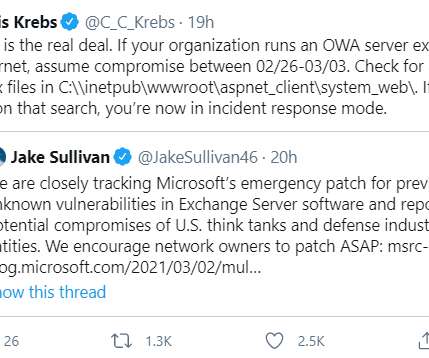
On March 2, Microsoft released emergency security updates to plug four security holes in Exchange Server versions 2013 through 2019 that hackers were actively using to siphon email communications from Internet-facing systems running Exchange. The web shell gives the attackers administrative access to the victim’s computer servers.


















Let's personalize your content