North Korea-linked campaign targets security experts via social media
Security Affairs
JANUARY 26, 2021
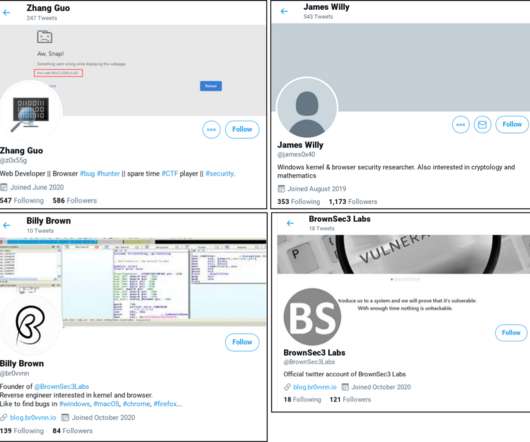
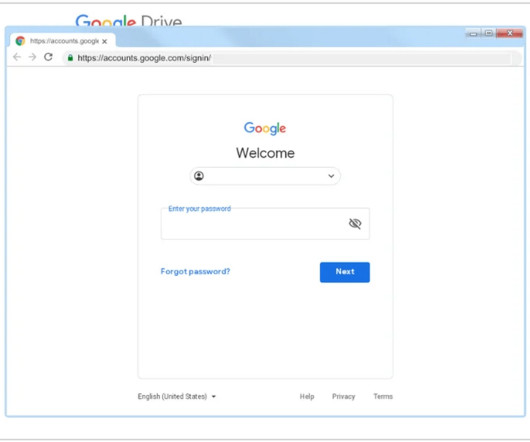
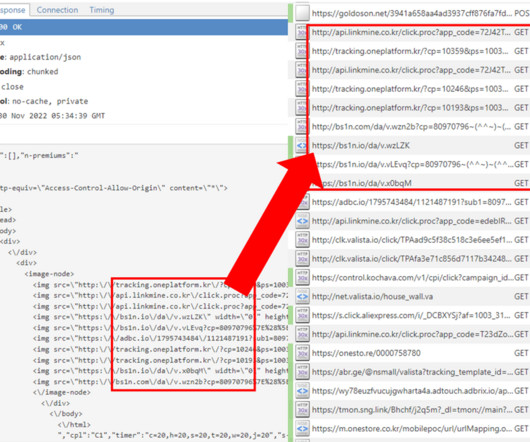
Google TAG is warning that North Korea-linked hackers targeting security researchers through social media. Google Threat Analysis Group (TAG) is warning that North Korea-linked hackers targeting security researchers through social media. ” reads the TAG’s report.
























Let's personalize your content