Pro-Russian hacker group KillNet plans to attack Italy on May 30
Security Affairs
MAY 29, 2022
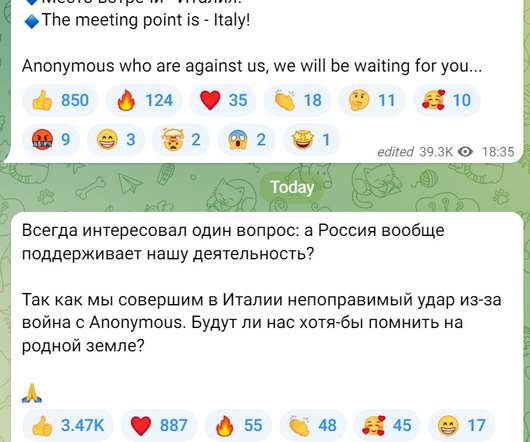
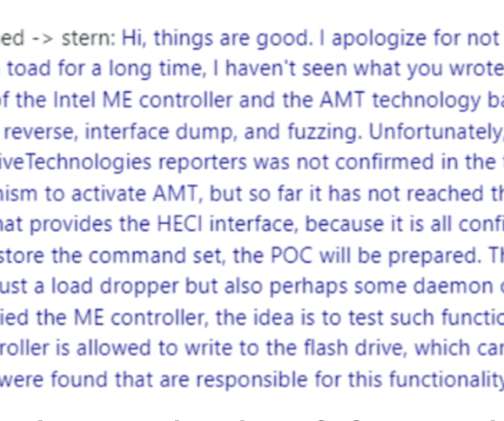
Now the group announced a massive attack against Italy, planned on Monday, 30 at 05:00, the collective is also challenging Anonymous which is their adversary. Please vote for Security Affairs and Pierluigi Paganini in every category that includes them (e.g. ” state the messages. To nominate, please visit:?. Pierluigi Paganini.






























Let's personalize your content