Expert found a backdoor in XZ tools used many Linux distributions
Security Affairs
MARCH 30, 2024
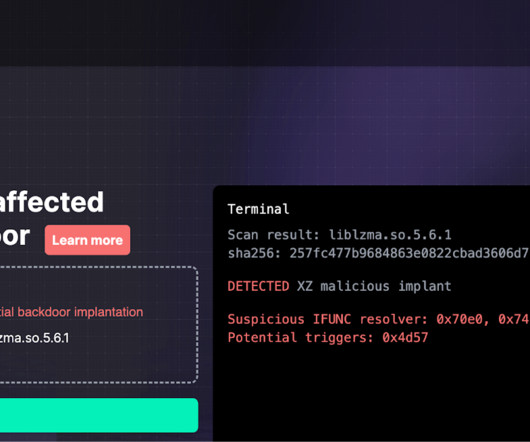
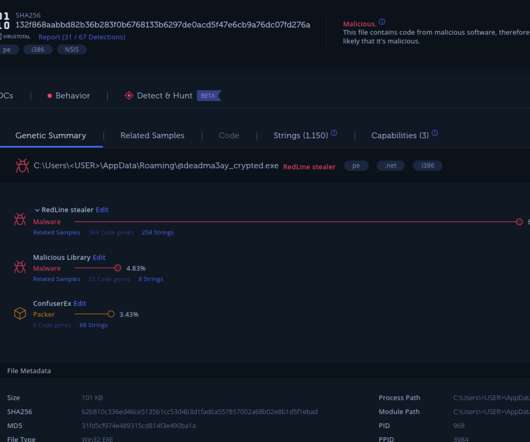
Red Hat warns of a backdoor in XZ Utils data compression tools and libraries in Fedora development and experimental versions. Red Hat urges users to immediately stop using systems running Fedora development and experimental versions because of a backdoor in the latest versions of the “xz” tools and libraries. x versions.












































Let's personalize your content