SYS01 stealer targets critical government infrastructure
Security Affairs
MARCH 7, 2023
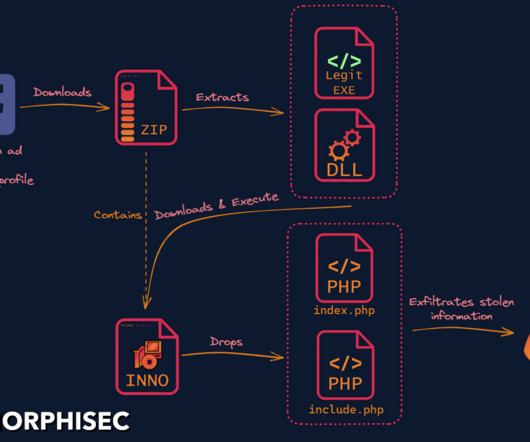
Researchers discovered a new info stealer dubbed SYS01 stealer targeting critical government infrastructure and manufacturing firms. The last stage malware is the PHP-based SYS01stealer malware which is able to steal browser cookies and abuse authenticated Facebook sessions to steal information from the victim’s Facebook account.








































Let's personalize your content