Arrests in $400M SIM-Swap Tied to Heist at FTX?
Krebs on Security
FEBRUARY 1, 2024
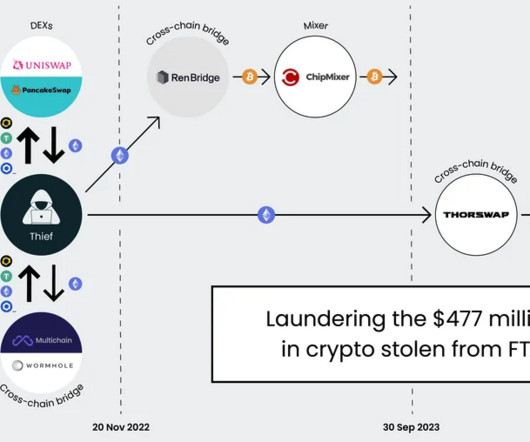
government did not name the victim organization, but there is every indication that the money was stolen from the now-defunct cryptocurrency exchange FTX , which had just filed for bankruptcy on that same day. 11-12, 2022. 11, 2022 after they SIM-swapped an AT&T customer by impersonating them at a retail store using a fake ID.




























Let's personalize your content