Arrests in $400M SIM-Swap Tied to Heist at FTX?
Krebs on Security
FEBRUARY 1, 2024
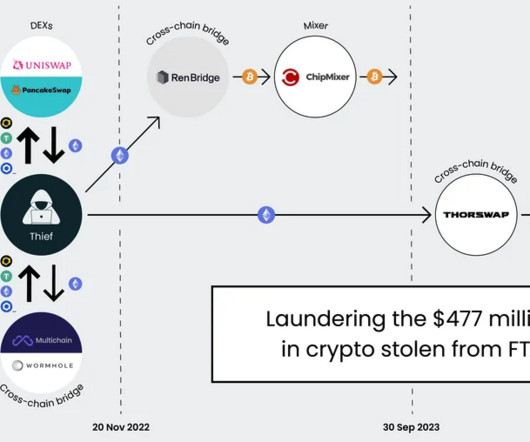
11-12, 2022. ” Colorado resident Emily “Em” Hernandez allegedly helped the group gain access to victim devices in service of SIM-swapping attacks between March 2021 and April 2023. . 11, 2022 after they SIM-swapped an AT&T customer by impersonating them at a retail store using a fake ID. 2, 2024.





















Let's personalize your content