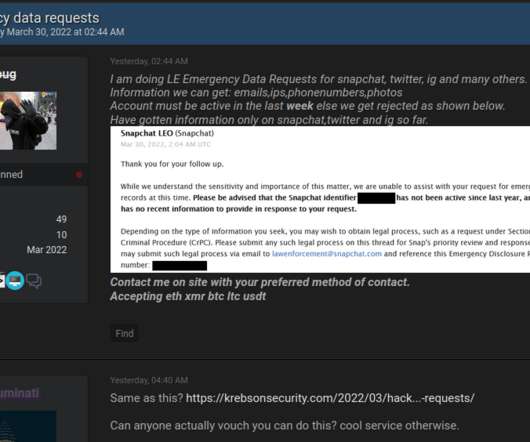
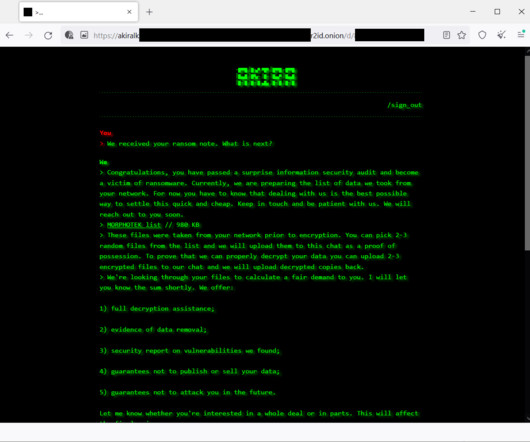
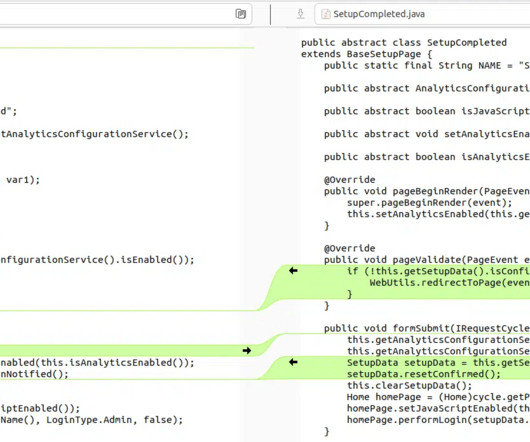
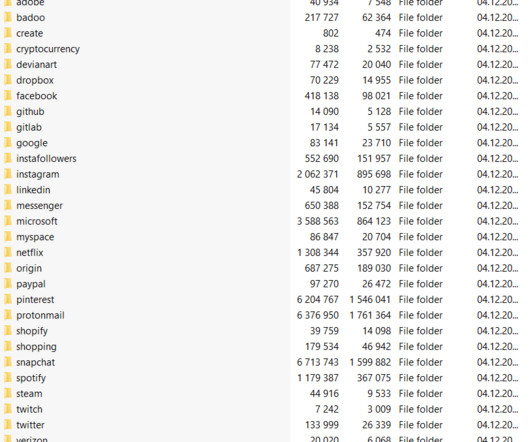
GUEST ESSAY: Everything you should know about the cybersecurity vulnerabilities of AI chatbots
The Last Watchdog
FEBRUARY 20, 2024
These tools saved 2.5 Microsoft Bot Framework: Microsoft’s offering is a robust platform providing bot development, deployment and management tools. Authentication and authorization vulnerabilities: Weak authentication methods and compromised access tokens can provide unauthorized access. per interaction.










































Let's personalize your content