Wannacry, the hybrid malware that brought the world to its knees
Security Affairs
OCTOBER 31, 2022
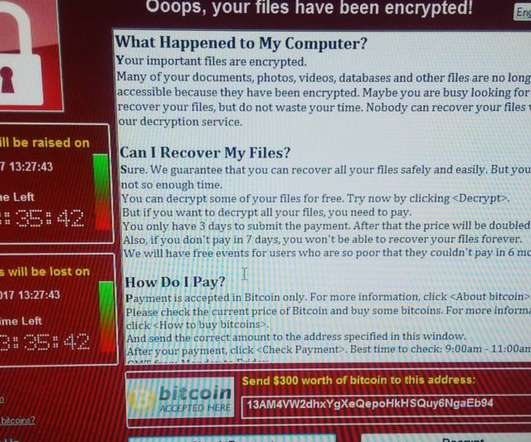
In the early afternoon of Friday 12 May 2017, the media broke the news of a global computer security attack carried out through a malicious code capable of encrypting data residing in information systems and demanding a ransom in cryptocurrency to restore them, the Wannacry ransomware. The operating algorithm was RSA.





















Let's personalize your content