GUEST ESSAY: Too many SMBs continue to pay ransomware crooks — exacerbating the problem
The Last Watchdog
FEBRUARY 20, 2023
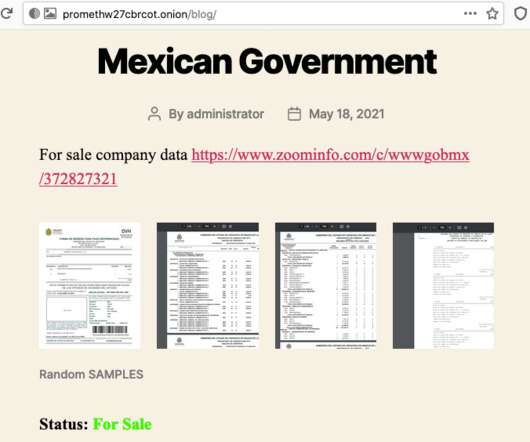
One report showed ransomware attacks increased by 80 percent in 2022, with manufacturing being one of the most targeted industries. The Glenn County Office of Education in California suffered an attack limiting access to its own network. Follow him on Twitter or LinkedIn for more articles on emerging cybersecurity trends.






































Let's personalize your content