Chinese actor ‘Unfading Sea Haze’ remained undetected for five years
Security Affairs
MAY 23, 2024
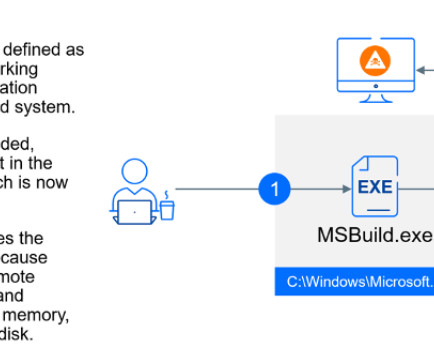
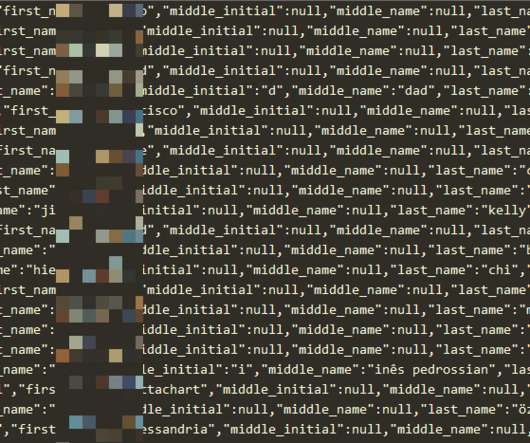
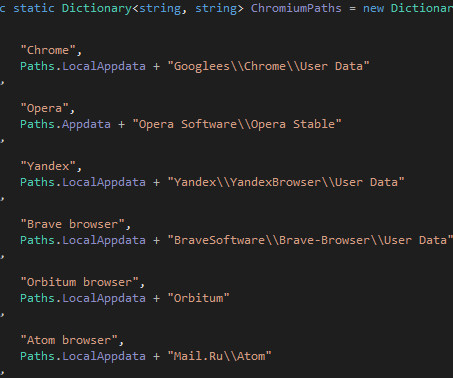
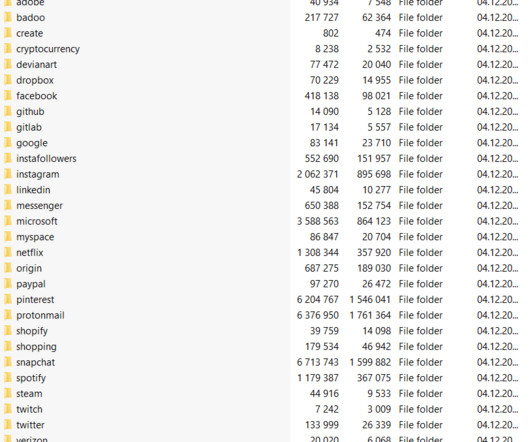
The messages use specially crafted archives containing LNK files disguised as regular documents. These archives mimicked the installation process of Microsoft Defender or exploited current US political issues. ” The threat actors used both custom malware and off-the-shelf tools to gather sensitive data from victim machines.






























Let's personalize your content