Autonomous cloud operations
OpenText Information Management
APRIL 19, 2024
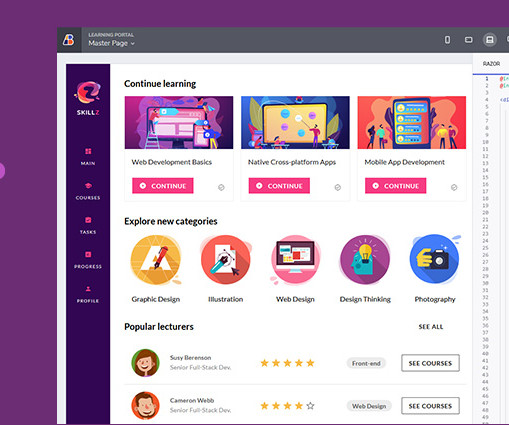
Skye has spent the last six months working with IT departments to better understand current and future needs for cloud operations. You: What is going on in IT departments around the globe? SKYE: Limited resources, too many priorities, AI creating new parameters and needs. You: What’s top of mind today for CIOs?


















































Let's personalize your content