New AlienFox toolkit harvests credentials for tens of cloud services
Security Affairs
MARCH 30, 2023
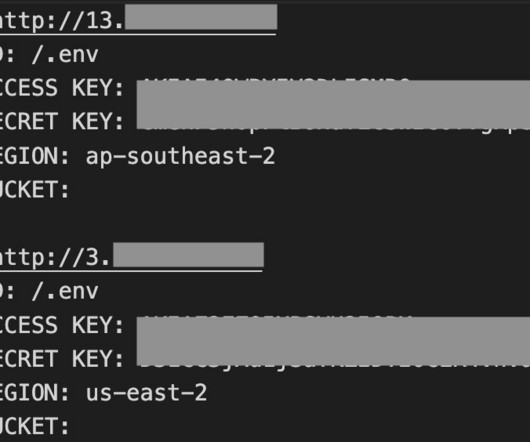
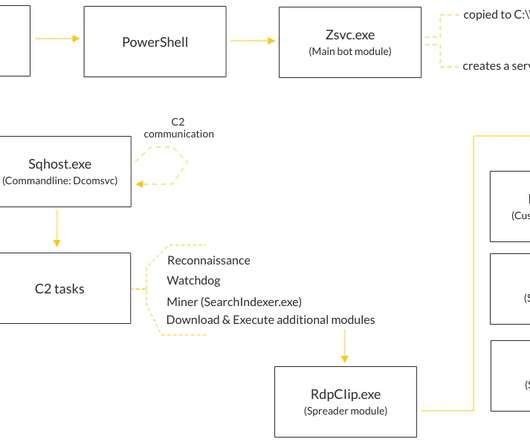
The most recent version of AlienFox, Version 4, shows a totally different structure, it has added WordPress, Joomla, Drupal, Prestashop, Magento, and Opencart targeting, an Amazon.com retail site account checker. ” continues the analysis. Tool1, Tool2). There is a core script in the AlienFox root directory named ALIENFOXV4.py





















Let's personalize your content