New AlienFox toolkit harvests credentials for tens of cloud services
Security Affairs
MARCH 30, 2023
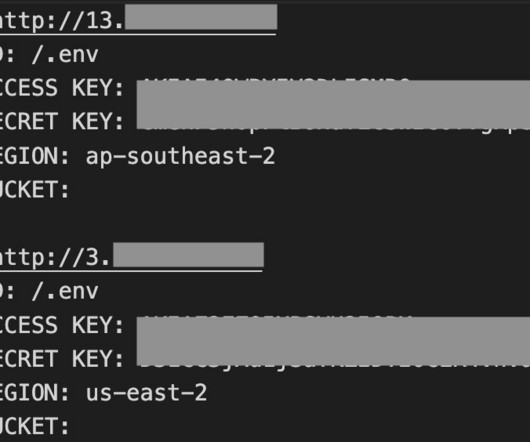
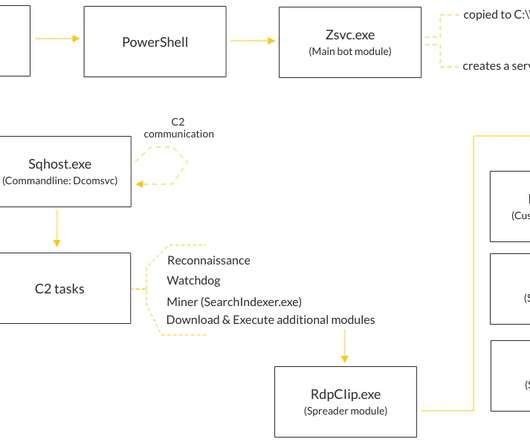
AlienFox collects lists of misconfigured cloud endpoints through security scanning platforms like LeakIX and SecurityTrails. The most recent version of AlienFox, Version 4, shows a totally different structure, it has added WordPress, Joomla, Drupal, Prestashop, Magento, and Opencart targeting, an Amazon.com retail site account checker.


















Let's personalize your content