NPM packages found containing the TurkoRat infostealer
Security Affairs
MAY 19, 2023
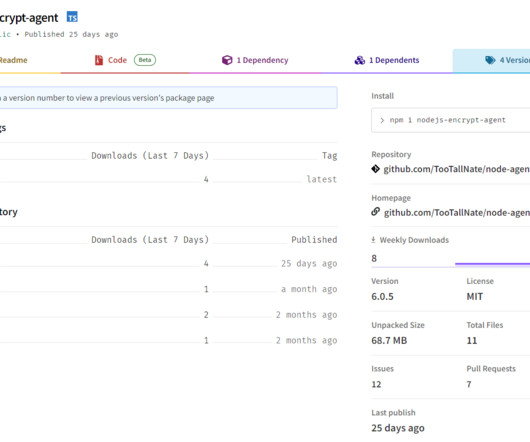
ReversingLabs discovered two malicious packages, respectively named nodejs-encrypt-agent and nodejs-cookie-proxy-agent, in the npm package repository containing an open-source info-stealer called TurkoRat. The malware also supports anti-sandbox and analysis functionalities to avoid detection and prevent being analyzed.











































Let's personalize your content