How to Prevent Malware Attacks: 8 Tips for 2023
IT Governance
APRIL 5, 2023
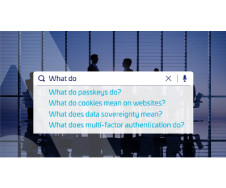
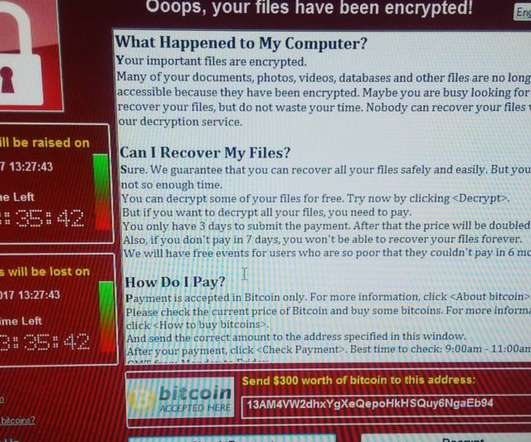
It can do this in a number of ways, such as: Stealing, encrypting or deleting sensitive information; Hijacking or altering core system functions; Monitoring user activity; and Spamming the device with adverts. Ransomware spreads through a target’s systems, encrypting files as it goes. What is malware?














































Let's personalize your content