Stayin’ Alive campaign targets high-profile Asian government and telecom entities. Is it linked to ToddyCat APT?
Security Affairs
OCTOBER 13, 2023
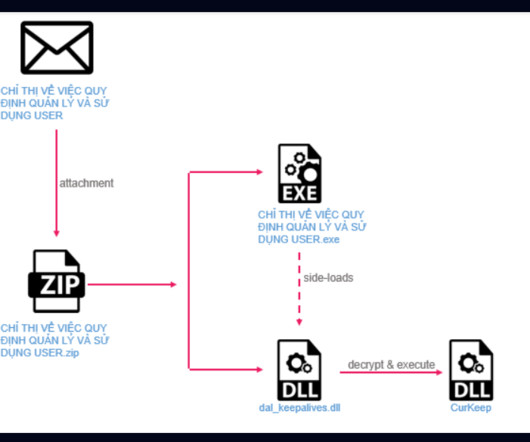
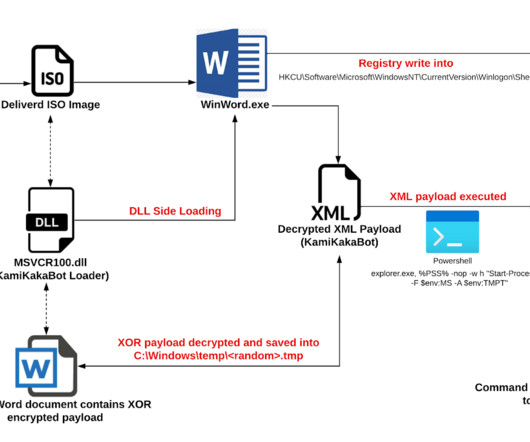
A cyberespionage campaign, tracked as Stayin’ Alive, targeted high-profile government and telecom entities in Asia. ” reads the analysis published by Checkpoint. shell – Sends the computer name in a JSON format encrypted with simple XOR encryption and base64 encoded to the C2. Is it linked to ToddyCat APT?









































Let's personalize your content