New HiatusRAT campaign targets Taiwan and U.S. military procurement system
Security Affairs
AUGUST 21, 2023
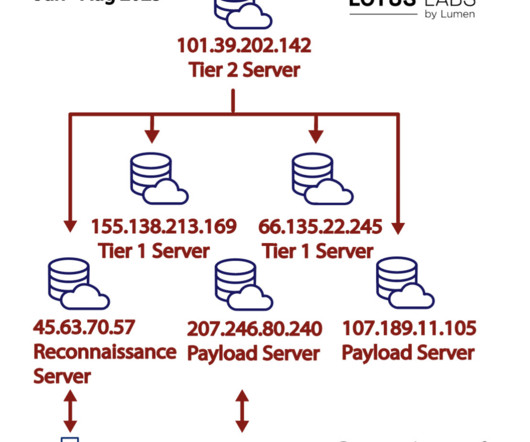
military procurement system. Threat actors leveraged edge routers, or “living on the edge” access, to passively collect traffic and set up a covert C2 infrastructure. Threat actors leveraged edge routers, or “living on the edge” access, to passively collect traffic and set up a covert C2 infrastructure. 57 155.138.213[.]169














































Let's personalize your content