A new piece of Ryuk Stealer targets government, military and finance sectors
Security Affairs
JANUARY 26, 2020
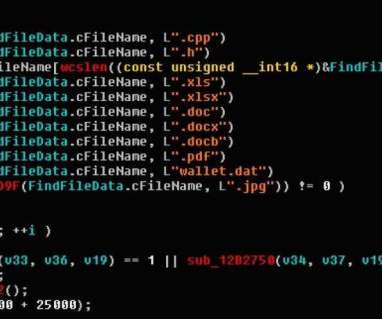
A new piece of the Ryuk malware has been improved to steal confidential files related to the military, government, financial statements, and banking. Targeted keywords in the new variant of the Ryuk stealer confirm that attackers are looking for confidential information in military, banking, finance and law enforcement.
























Let's personalize your content