The Future of Payments Security
Thales Cloud Protection & Licensing
JANUARY 26, 2021
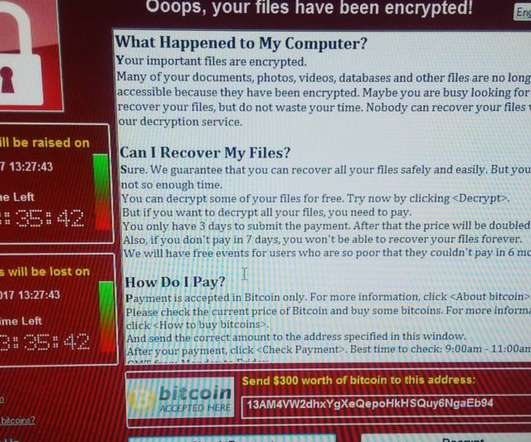
The Future of Payments Security. Even when banking organizations are upgrading security posture to safeguard sensitive financial information, hackers can steal the data intelligently by tying known vulnerabilities together, and making it turn out to be a potential attack. Securing digital transactions. Tue, 01/26/2021 - 09:17.




















Let's personalize your content