More on NSO Group and Cytrox: Two Cyberweapons Arms Manufacturers
Schneier on Security
DECEMBER 20, 2021
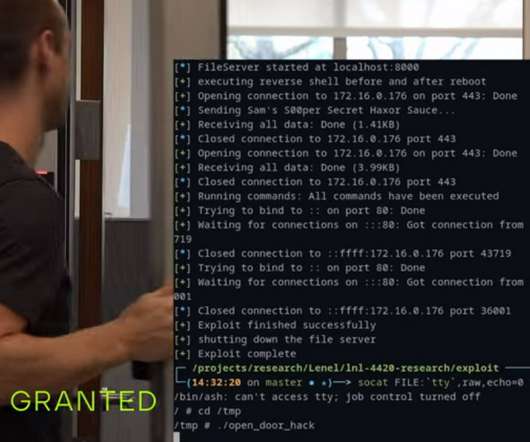
The other was hacked both by Pegasus and by the spyware from another cyberweapons arms manufacturer: Cytrox. ” In related news, Google’s Project Zero has published a detailed analysis of NSO Group’s zero-click iMessage exploit: FORCED ENTRY. One was hacked by NSO Group’s Pegasus spyware.

































Let's personalize your content