Malicious PDF Analysis
Security Affairs
FEBRUARY 13, 2019
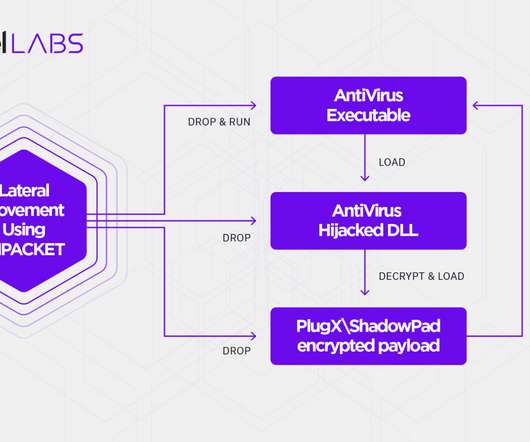
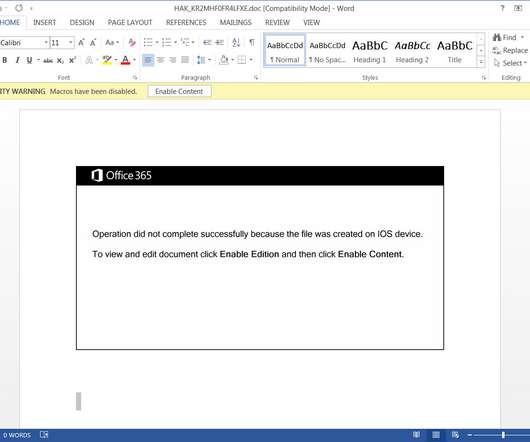
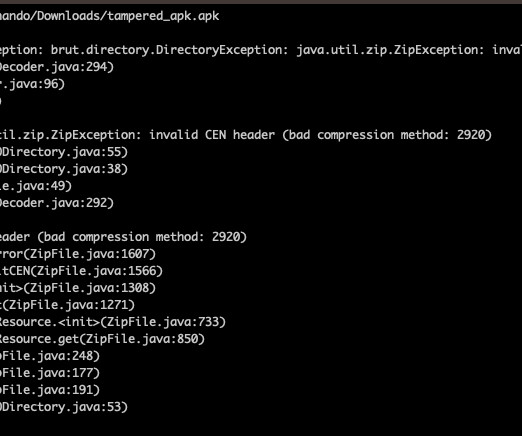
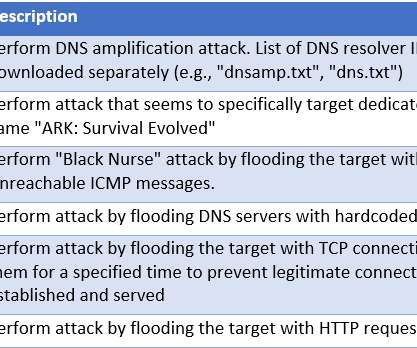
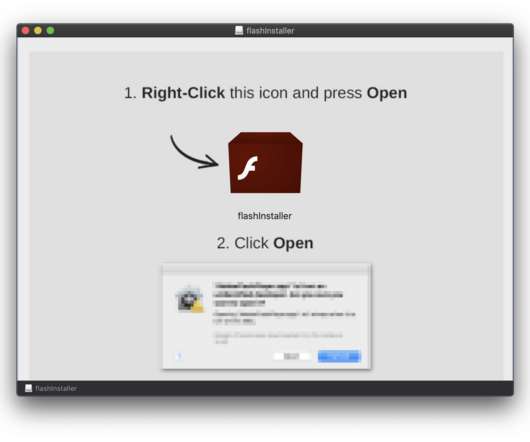
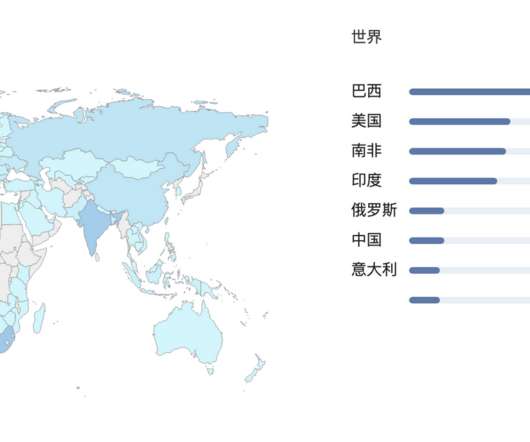
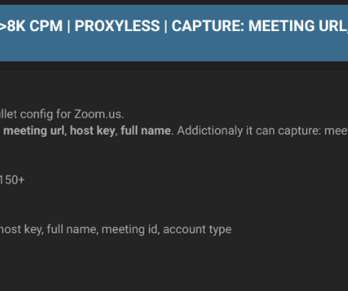
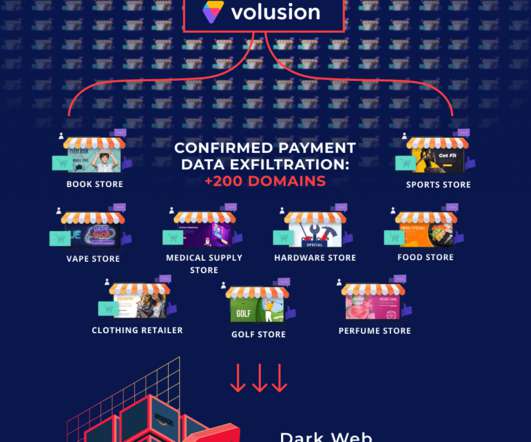
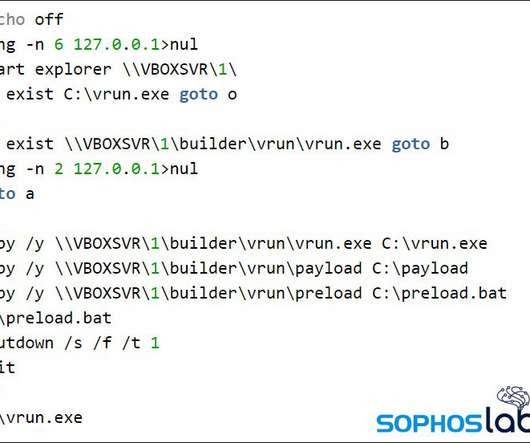
In the last few days I have done some analysis on malicious documents, especially PDF. Then I thought, “Why not turn a PDF analysis into an article?” Most security tools must always be adapted to this new reality of attack and infection. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.































Let's personalize your content