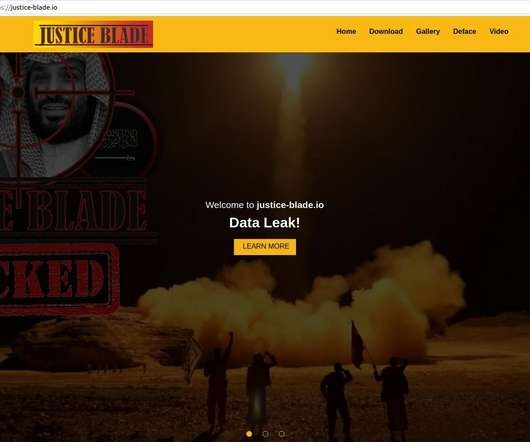
‘Justice Blade’ Hackers are Targeting Saudi Arabia
Security Affairs
NOVEMBER 7, 2022
The group of threat actors calling themselves ‘Justice Blade’ published leaked data from Smart Link BPO Solutions, an outsourcing IT vendor working with major enterprises and government agencies in the Kingdom of Saudi Arabia and other countries in the GCC.





















Let's personalize your content