Fake Used-Car Flyer for 2011 BMW Phishes Diplomats in Kyiv
Data Breach Today
JULY 12, 2023
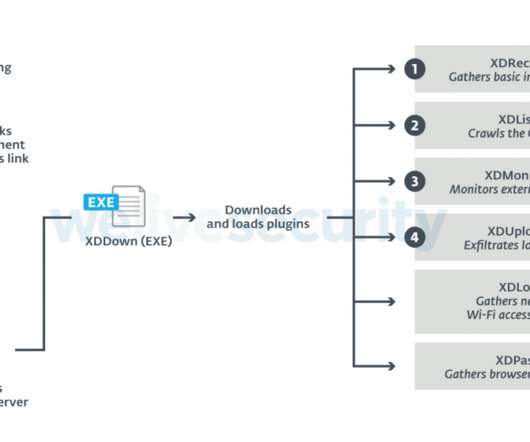
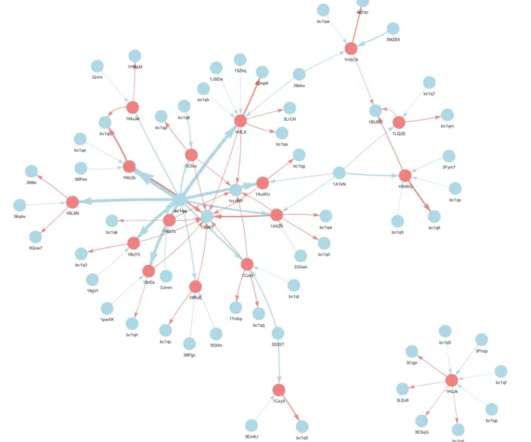
Campaign Targets 22 Embassies; Unit 42 Ties It to Russian Foreign Intelligence Diplomats in Ukraine shopping for used cars have been targeted with a listing for a "very good condition, low-fuel consumption" 2011 BMW 5 Series.













































Let's personalize your content