One Out of 10 Threats Still Make It All the Way to the Endpoint
KnowBe4
DECEMBER 30, 2022
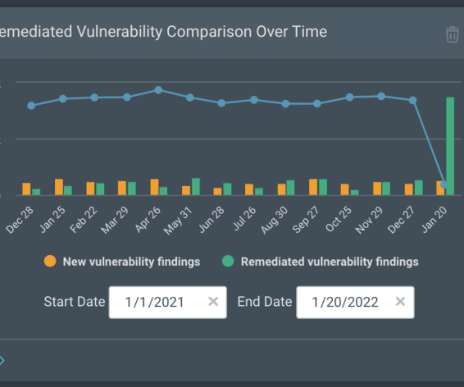
Despite good intentions, layered security measures, and efficacy claims by security solution vendors, new data shows that email-based threats are still getting all the way to the Inbox.

















































Let's personalize your content