New Report on IoT Security
Schneier on Security
SEPTEMBER 28, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Schneier on Security
SEPTEMBER 28, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”

Thales Cloud Protection & Licensing
NOVEMBER 6, 2019
As most of us know, IoT devices are on the rise in enterprise networks. According to McKinsey & Company , the proportion of organizations that use IoT products has grown from 13 percent in 2014 to 25 percent today. The issue is that these tens of billions of new devices will likely amplify the inherent security risks of IoT.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
MARCH 28, 2019
Related: IoT botnets now available for economical DDoS blasts. Here we are in 2019 and the same attack strategy continues to persist. This attacker easily located IoT devices that used the manufacturers’ default security setting. Beyond DDoS. In fact, it can be argued that the opposite is happening. Barest tip.

Thales Cloud Protection & Licensing
OCTOBER 19, 2022
Manufacturing needs to adopt a Zero Trust approach to mitigate increased cyber threats. Long gone is the time when manufacturing systems and operations were siloed from the Internet and, therefore, were not a cybersecurity target. Thu, 10/20/2022 - 06:20. Survey’s key findings.

Thales Cloud Protection & Licensing
JULY 15, 2021
Key Developments in IoT Security. Remember the early days of the emergence of Internet of Things (IoT) devices? Vulnerabilities have been discovered in many of these IoT devices. Ellen has extensive experience in cybersecurity, and specifically, the understanding of IoT risk. Thu, 07/15/2021 - 10:09.

Troy Hunt
NOVEMBER 25, 2020
In part 1 of this series, I posited that the IoT landscape is an absolute mess but Home Assistant (HA) does an admirable job of tying it all together. As with the rest of the IoT landscape, there's a lot of scope for improvement here and also just like the other IoT posts, it gets very complex for normal people very quickly.

IBM Big Data Hub
FEBRUARY 19, 2024
The pandemic and its aftermath highlighted the importance of having a robust supply chain strategy , with many companies facing disruptions due to shortages in raw materials and fluctuations in customer demand. Here’s how companies are using different strategies to address supply chain management and meet their business goals.

The Last Watchdog
NOVEMBER 15, 2018
Even as enterprises across the globe hustle to get their Internet of Things business models up and running, there is a sense of foreboding about a rising wave of IoT-related security exposures. And, in fact, IoT-related security incidents have already begun taking a toll at ill-prepared companies. Tiered performances.

IBM Big Data Hub
JUNE 20, 2023
Here’s what you need to know in order to build a successful strategy. We’ll go deeper into EAMs, the technologies underpinning them and their implications for asset lifecycle management strategy in another section. What is an asset? First, let’s talk about what an asset is and why they are so important.

The Last Watchdog
FEBRUARY 21, 2024
Related: How decentralized IoT boosts decarbonization Yet, more so than ever, infusing trustworthiness into modern-day digital services has become mission critical for most businesses. If you factor in where we are in the world today with things like IoT, quantum computing and generative AI, we could be heading for a huge trust crisis.”

OpenText Information Management
OCTOBER 16, 2024
Traditional maintenance strategies often rely on reactive approaches, addressing issues only after machinery breaks down. For industries like manufacturing, healthcare, and energy, this downtime doesn't just mean a temporary hiccup; it leads to significant financial losses, decreased productivity, and even safety risks.

eSecurity Planet
FEBRUARY 2, 2024
Within the last couple of months, smart device vulnerabilities have been piling up, prompting businesses to protect their Internet of Things (IoT) environments. While Teslas aren’t the typical business IoT device, their connection to the internet makes them a cyber threat as much as your business’s other IoT technology.

IBM Big Data Hub
MAY 31, 2023
There are many overlapping business usage scenarios involving both the disciplines of the Internet of Things (IoT) and edge computing. This is especially true in manufacturing and industrial engineering. From strategy to design, development and deployment, there is a lot of thought that goes into connecting physical products.

Thales Cloud Protection & Licensing
MAY 30, 2018
The recent DHS Cybersecurity Strategy was released at a crucial time when today’s cyberspace has become a new frontier for warfare for both nation states and criminal hackers. The key to successfully applying the first two pillars of the strategy includes evaluating cyberthreats quickly and mitigating risks or remediating threats swiftly.

Thales Cloud Protection & Licensing
AUGUST 16, 2018
On May 16, the Department of Homeland Security (DHS) released a new cybersecurity strategy to keep pace with the evolving cyber risk landscape. As we inch closer to the mid-term elections in November, I wanted to share what I hope (expect) to see as part of this strategy going forward.

Thales Cloud Protection & Licensing
DECEMBER 13, 2018
Invariably, Internet of Things (IoT) strategies form the backbone of those efforts. Enormous quantities of data can be generated by and collected from a wide variety of IoT devices. The diversity of IoT devices and lack of standardisation also poses challenges. The goal is then to analyse it and take impactful action.

IBM Big Data Hub
JANUARY 15, 2024
And while no one digital transformation strategy will be like any other, here are some recurring trends that help organizations engage in successful digital transformation initiatives. The Internet of Things (IoT) enables technologies to connect and communicate with each other.

Thales Cloud Protection & Licensing
AUGUST 24, 2021
Years before the pandemic struck, organizations first began adding Internet of Things (IoT) along with Industrial Internet of Things (IIoT) devices to their networks. How can you have a conversation about IoT and IIoT security without referencing the user? They all inform IoT and IIoT security as a business priority. Compliance.

eSecurity Planet
NOVEMBER 19, 2021
IoT security is where endpoint detection and response ( EDR ) and enterprise mobility management ( EMM ) meet the challenges of a rapidly expanding edge computing infrastructure. As the enterprise attack surface grows, IoT is yet another attack vector organizations aren’t fully prepared to defend.

The Last Watchdog
MARCH 31, 2021
From the known compromise vectors to the most recent threats, hackers are constantly on the lookout for new strategies to bypass IT notice, out maneuver defense setups, and take advantage of new weaknesses. This method enables attackers to bypass the popular detection strategies that can potentially scan and spot harmful attachments.

Data Matters
MARCH 7, 2022
If adopted in its current form, the new rules will impose far-reaching obligations on tech companies (such as manufacturers of connected products and cloud service providers) and give national authorities new enforcement powers to sanction infringements with fines of up to EUR 20 million or 4% of annual global revenue, whichever is higher.

OpenText Information Management
APRIL 1, 2024
Mark will be joined by OpenText customer Carsten Trapp, CIO of manufacturer Carl Zeiss, who will discuss his company’s partnership with OpenText to support their SAP S/4HANA transformation and compliance initiatives. While you’re wandering the show floor, take time out to see AI in action at the Aviator IoT LEGO® Experience.

IBM Big Data Hub
JUNE 30, 2023
80% of manufacturers report MRO asset management in their facilities needs improvement 60% of construction companies admit their industry is behind when it comes to adopting digital technology 5 ways the industrial sector can improve its supply chain resiliency 1. This equipment is critical to expanding capacity for chip production.

eSecurity Planet
FEBRUARY 23, 2022
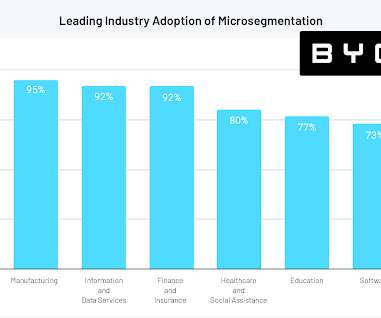
Industries with very expensive operational technology (OT) and Internet of Things (IoT) devices, such as healthcare or industrial manufacturing, can be especially vulnerable. Also read: Top IoT Security Solutions for 2022. Researchers estimate that 90% of healthcare IoT critical risks can be addressed by network segmentation.
eSecurity Planet
NOVEMBER 11, 2021
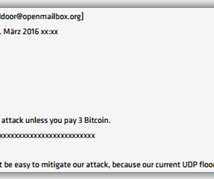
It’s one of the most powerful botnets in history, and it acts similarly (not exactly) as the Mirai botnet , exploiting vulnerabilities in IoT devices and networks. Meris may have infected more than 250,000 devices manufactured by Mikrotik, a Latvian company that develops routers and wireless ISP systems. Ransom Now a DDoS Strategy.

eSecurity Planet
MARCH 1, 2023
It involves a variety of strategies and practices designed to preserve the confidentiality, integrity and availability of wireless networks and their resources. This works by allowing the IoT device to present a QR code or a Near Field Communication (NFC) tag, which the user can scan with their device to establish a secure Wi-Fi connection.

The Last Watchdog
FEBRUARY 21, 2020
We’re not just talking about website clicks; PKI comes into play with respect to each of the millions of computing instances and devices continually connecting to each other – the stuff of DevOps and IoT. It can be as granular as a microservice in a software container connecting to a mobile app, for instance.
eSecurity Planet
NOVEMBER 10, 2021
The idea of walling off the most critical assets in a network is a particularly good fit for critical infrastructure and industrial IoT, in which a wide range of legacy devices simply aren’t able to run traditional EDR software. Critical Infrastructure, IIoT a Good Fit. “The companies are reliant on the perimeter.”

IBM Big Data Hub
AUGUST 8, 2023
This ambitious bill, largely managed by the US Department of Transportation, will distribute USD 1 trillion to fund construction, manufacturing initiatives and public works. Both strategies help enterprises better plan for maintenance and avoid costly shutdowns that can impact the entire business.

IBM Big Data Hub
FEBRUARY 7, 2024
1 In pursuit of net zero, organizations will focus their sustainability efforts on two paths in 2024: Clean energy : The transition from fossil fuels to renewable energy sources is central to sustainability strategies and net zero initiatives, and was a central issue last year at the United Nations’ COP28 climate summit.

Information Matters
DECEMBER 7, 2017
Finding “reliable” data about the installed base of Internet of Things (IoT) devices, market size and forecasts is not easy and can be expensive if you have to buy a commercial market report. Creating IoT stats is notoriously difficult depending on accuracy of models, assumptions and definitions. billion in 2018, an increase of 14.6%

Thales Cloud Protection & Licensing
DECEMBER 30, 2020
Speaking of the intersection of healthcare and technology, we released our case study with medical device manufacturer Candela. Behnam Tabrizi wrote a fantastic piece for Harvard Business Review encouraging companies to Put Employees at the Center of Your Post-Pandemic Digital Strategy. Behnam Tabrizi, Harvard Business Review.

IBM Big Data Hub
JANUARY 26, 2024
hereafter as Shuto Technology) to help a joint venture Original Equipment Manufacturer (OEM) in China to obtain information in an accurate and cost-effective way for on-site technicians. production systems, IoT platforms etc.) IBM® recently announced that it has worked with its business partner, Beijing Shuto Technology Co.,

Thales Cloud Protection & Licensing
DECEMBER 5, 2017
I also tapped some of my expert colleagues John Grimm, Sol Cates, Jose Diaz and Jon Geater to share their thoughts on a few areas including IoT, established and emerging technologies, and payments. Jose Diaz, Director of Payments Strategy, sees financial institutions keeping a close eye on fraud that could impact its customers.

CGI
FEBRUARY 9, 2016
Well personalisation has come a long way since then and car manufacturers allow you to select from a wide range of options, plus the ability to choose any paint colour you wish, meaning in today’s market, very few cars have the same specification. Add new comment. Blog moderation guidelines and term of use.

eSecurity Planet
SEPTEMBER 1, 2021
Service providers and 5G-enabled device manufacturers both have critical roles to play in the success and sustainability of this wireless network rollout. Exposing the Internet of Things (IoT) Universe. IoT products are notoriously vulnerable appliances because the build prioritizes ease of use and connectivity.

ARMA International
SEPTEMBER 13, 2021
The exponential growth in content is fueled by a plethora of connected devices, colloquially called “Internet of Things (IoT),” from cell phones, mobiles, and wearable technologies, to sensors in homes, appliances, cars, and so on. Consequently, CS are inextricably linked to a cloud-first strategy. Content Services Platforms (CSP).

CGI
FEBRUARY 19, 2019
This increase is consistent with almost half of the utilities executives interviewed revealing that they are extending their digital strategies to include a wider ecosystem of partners. partners with Google to use their data for solar generation and cost saving simulations, and with German battery manufacturer SOLARWATT for energy storage.

eSecurity Planet
OCTOBER 26, 2021
There is no such thing as an ironclad risk-averse software management strategy; therefore, organizations must strive to be risk-aware. Read more: Attackers Exploit Flaw that Could Impact Millions of Routers, IoT Devices. Proof of Concept: Healthcare SBOM.

Hunton Privacy
MARCH 2, 2023
On March 2, 2023, the Biden-Harris Administration announced the release of the National Cybersecurity Strategy. ONCD, in coordination with the Office of Management and Budget, will work to implement the Strategy under the oversight of National Security Council staff.

Thales Cloud Protection & Licensing
OCTOBER 10, 2022
These concepts are no longer limited to our mobile devices but are becoming increasingly important to operations in the manufacturing, transportation, and energy sectors. In fact, according to Gartner, the deployment of IoT devices will accelerate from 25 billion in 2023 to 75 billion in 2025. Manufacturing productivity.

eSecurity Planet
SEPTEMBER 9, 2024
Industrial control systems (ICS) are the backbone of critical infrastructure, powering essential operations in the energy, manufacturing, water treatment, and transportation sectors. These systems are integral to the smooth operation of industries such as manufacturing, power generation, oil and gas, water management, and more.
IBM Big Data Hub
MAY 31, 2023
Your maintenance strategy may not be the first thing that springs to mind when thinking about the bottom line. Yet, given that machinery, equipment and systems keep businesses running, maintenance strategies have a major role to play. Both strategies aim at reducing the risk of catastrophic or costly problems.

Collibra
APRIL 3, 2019
Continued adoption of IoT technologies will pose both opportunities and challenges. A tsunami of new data streams offers enormous opportunities in guiding digital transformation strategies across many industries. Any organisation engaged in IoT will be amassing datasets that have the potential to become extremely valuable.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content