Critical Apache Guacamole flaws expose organizations at risk of hack
Security Affairs
JULY 2, 2020
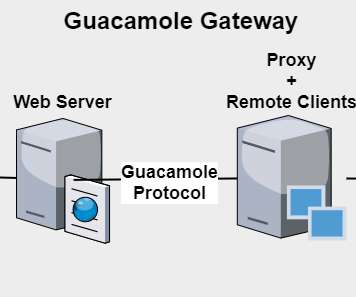
Security experts from Check Point Research have discovered multiple critical reverse RDP vulnerabilities in the Apache Guacamole, which is a clientless remote desktop gateway. It supports standard protocols like VNC, RDP, and SSH and allows system administrators to remotely access and manage Windows and Linux machines.






























Let's personalize your content